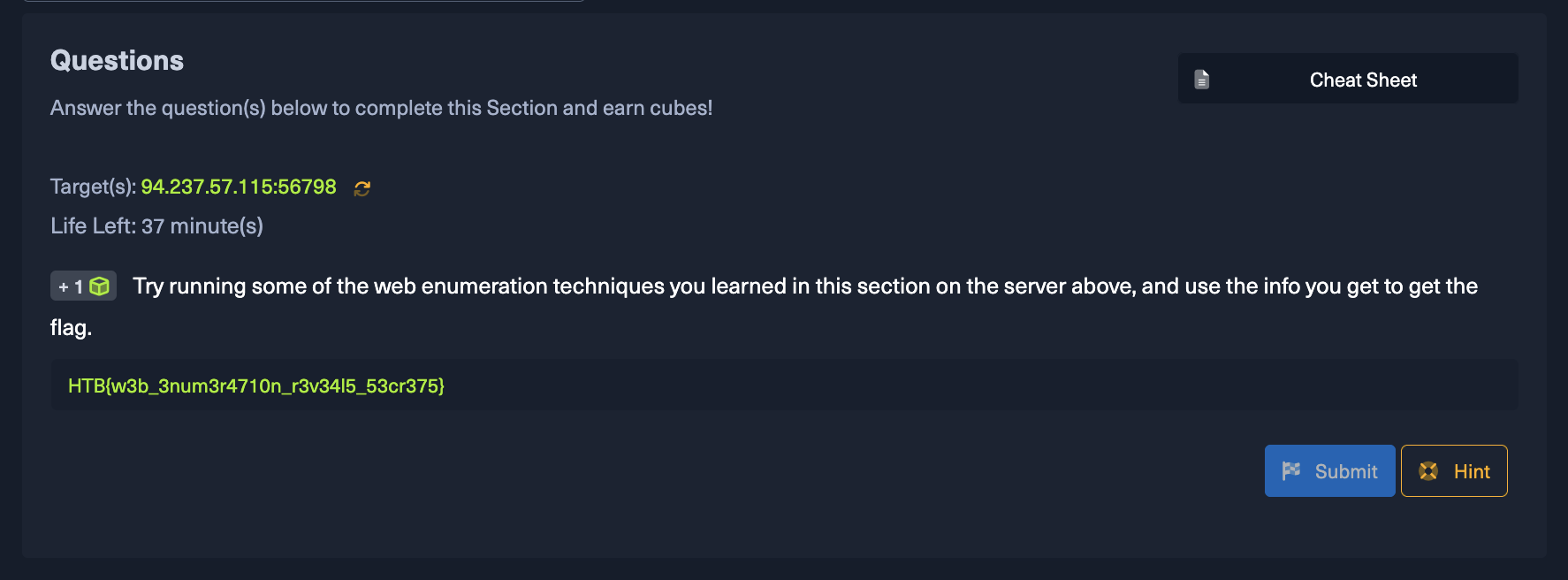
Instruction
Try running some of the web enumeration techniques you learned in this section on the server above, and use the info you get to get the flag.
Spawn the target and start the instance.
Recon
1. Curl
Check headers information using Curl. The output is indicate that the server is using Apache/2.4.41 (Ubuntu) based on the header information.
curl -IL 94.237.57.115:56798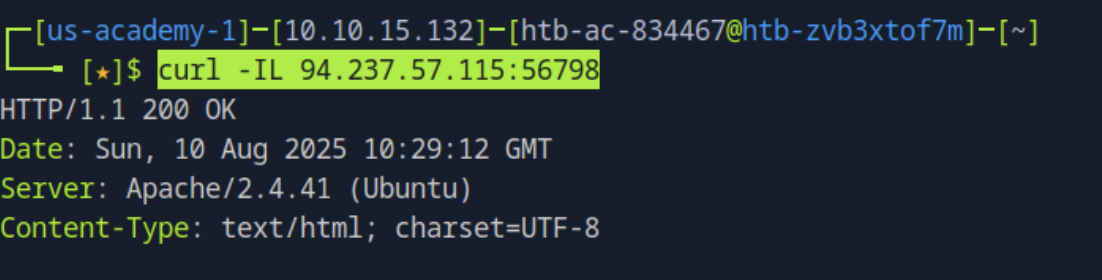 If you interest to know what -IL means, refer to the curl man page like below:
If you interest to know what -IL means, refer to the curl man page like below:
2. WhatWeb
Check the web technologies on using WhatWeb.
whatweb 94.237.57.115:56798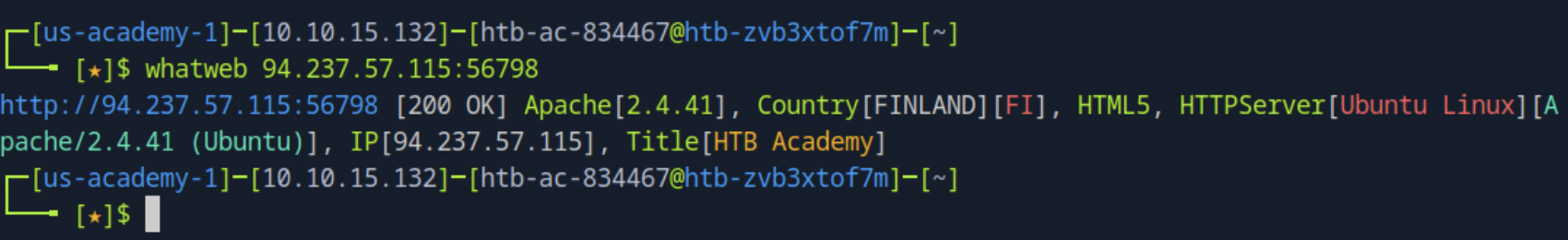
3. Directory and File enumeration
In this case we use GoBuster for this task. If you look at the command, it is using wordlist from SecLists
gobuster dir -u http://94.237.57.115:56798 -w /usr/share/seclists/Discovery/Web-Content/common.txt
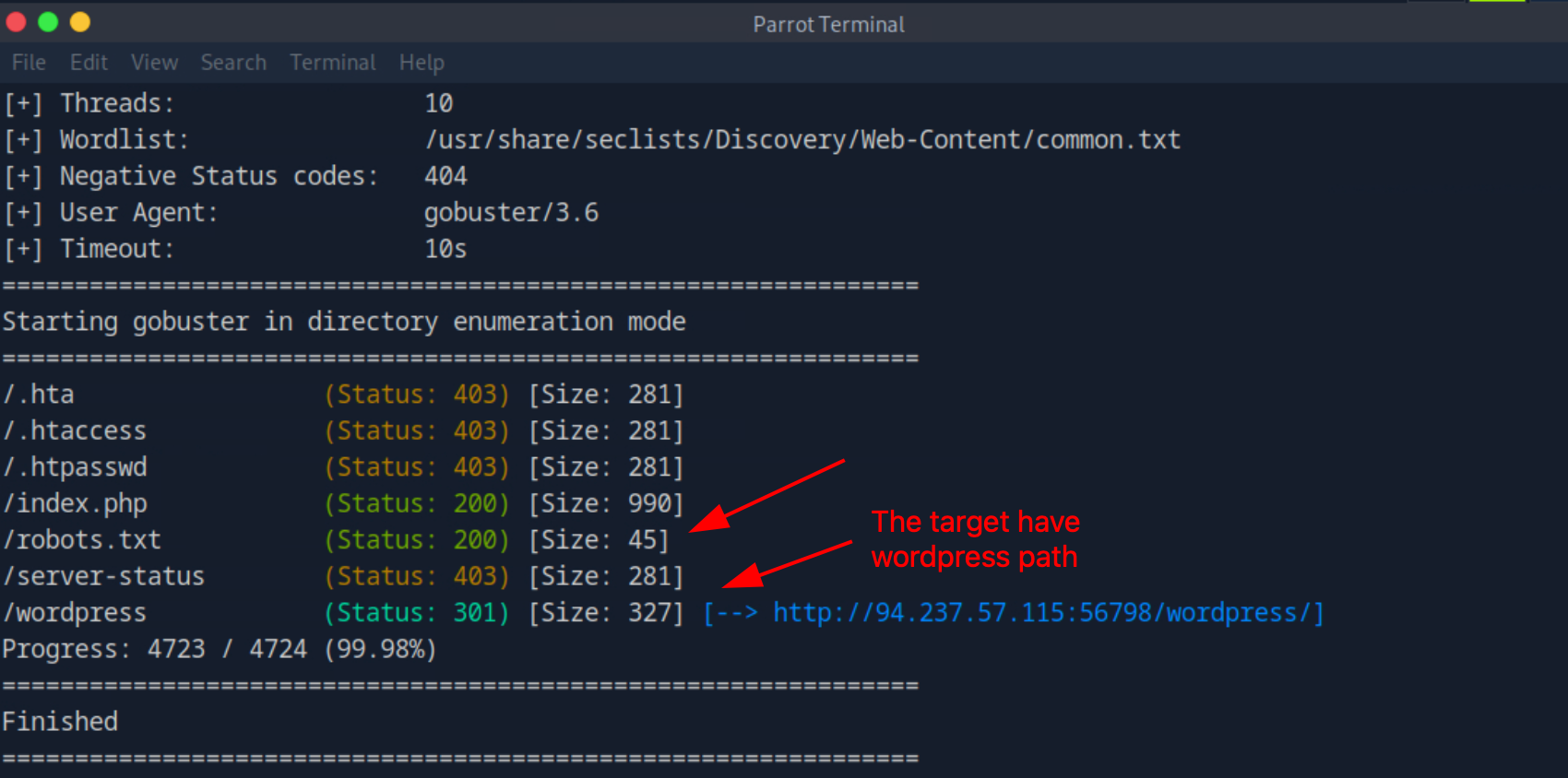
After running GoBuster using wordlists Web-Content/common.txt we found that the target is have a Wordpress path.
Investigate
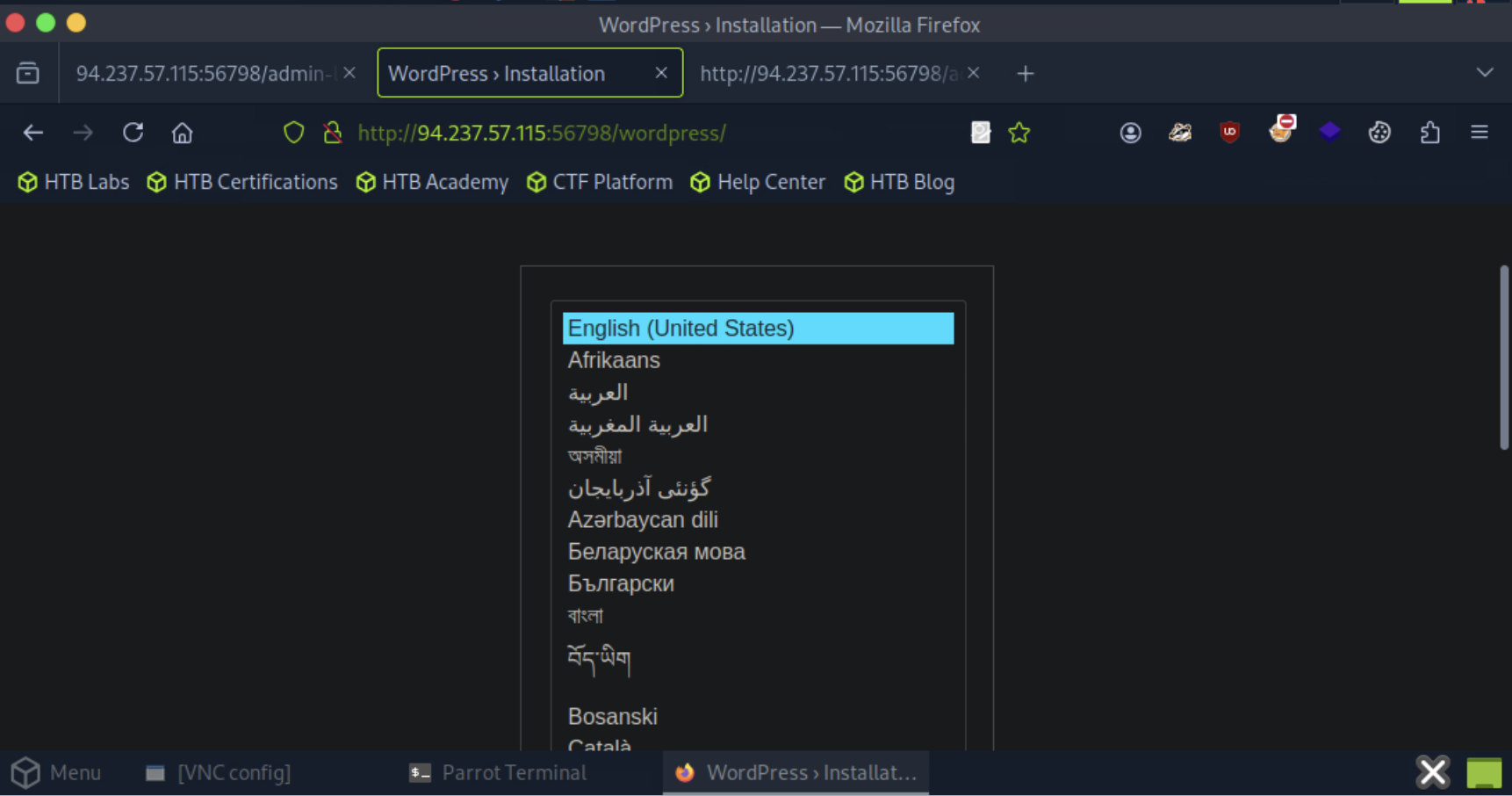
1. Wordpress path
If we open the /wordpress path, it looks like the Wordpress site is in setting mode, and not configured yet.
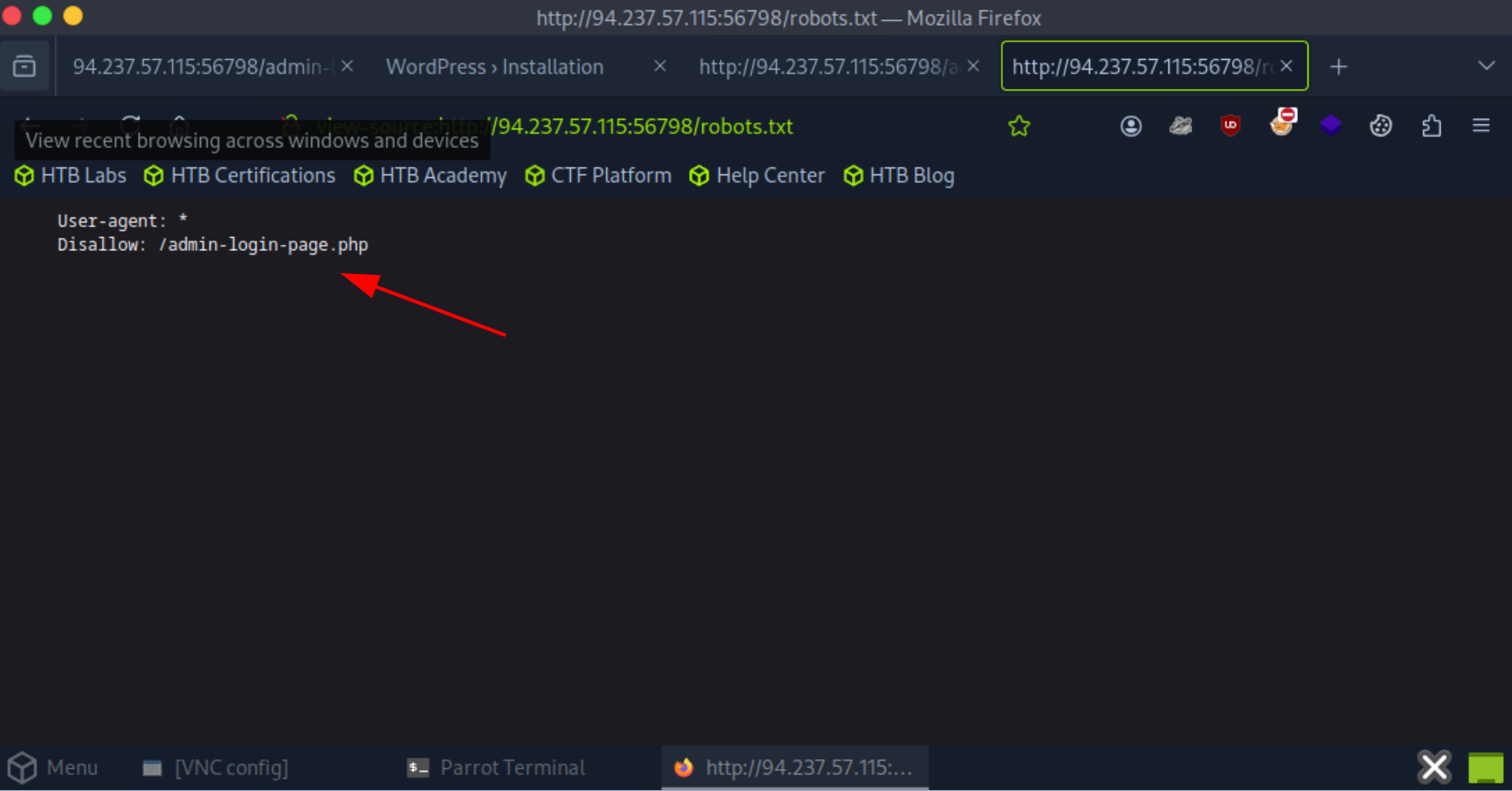
2. Robots.txt file
Next check the robots.txt by open the /robots.txt path in browser, we found something interesting. Indicate that the site have disallowed path named /admin-login-page.php
 Lets open the path in the browser.
Lets open the path in the browser.
3. Check Disallow path from robots.txt
Wow nice we found a login page with username and password.
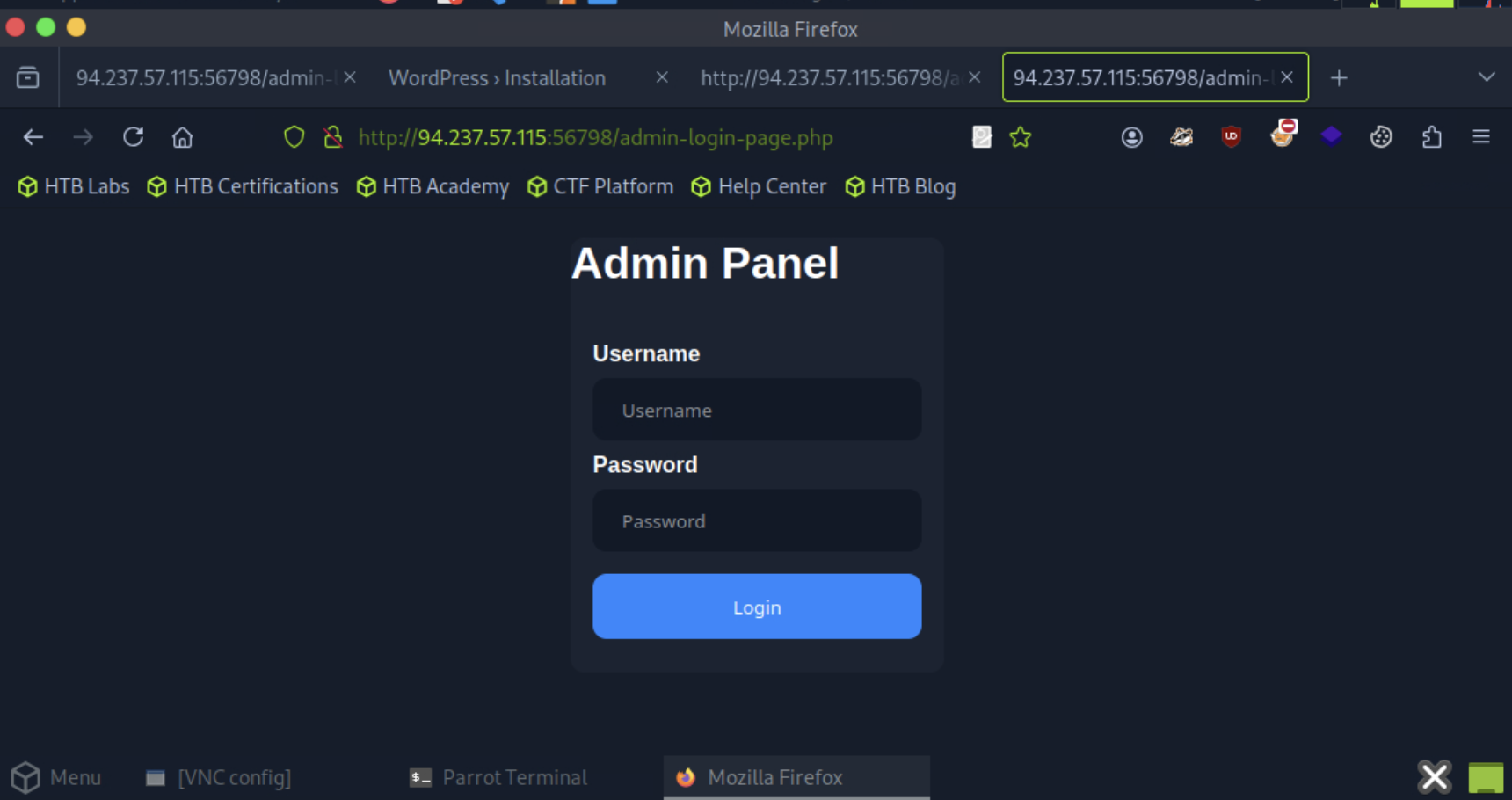 But looks like, we don’t have any credential yet for login in the web.
But looks like, we don’t have any credential yet for login in the web.
4. Investigating the source
Now try to investigate the page source by View Page Source like below from the Login page.
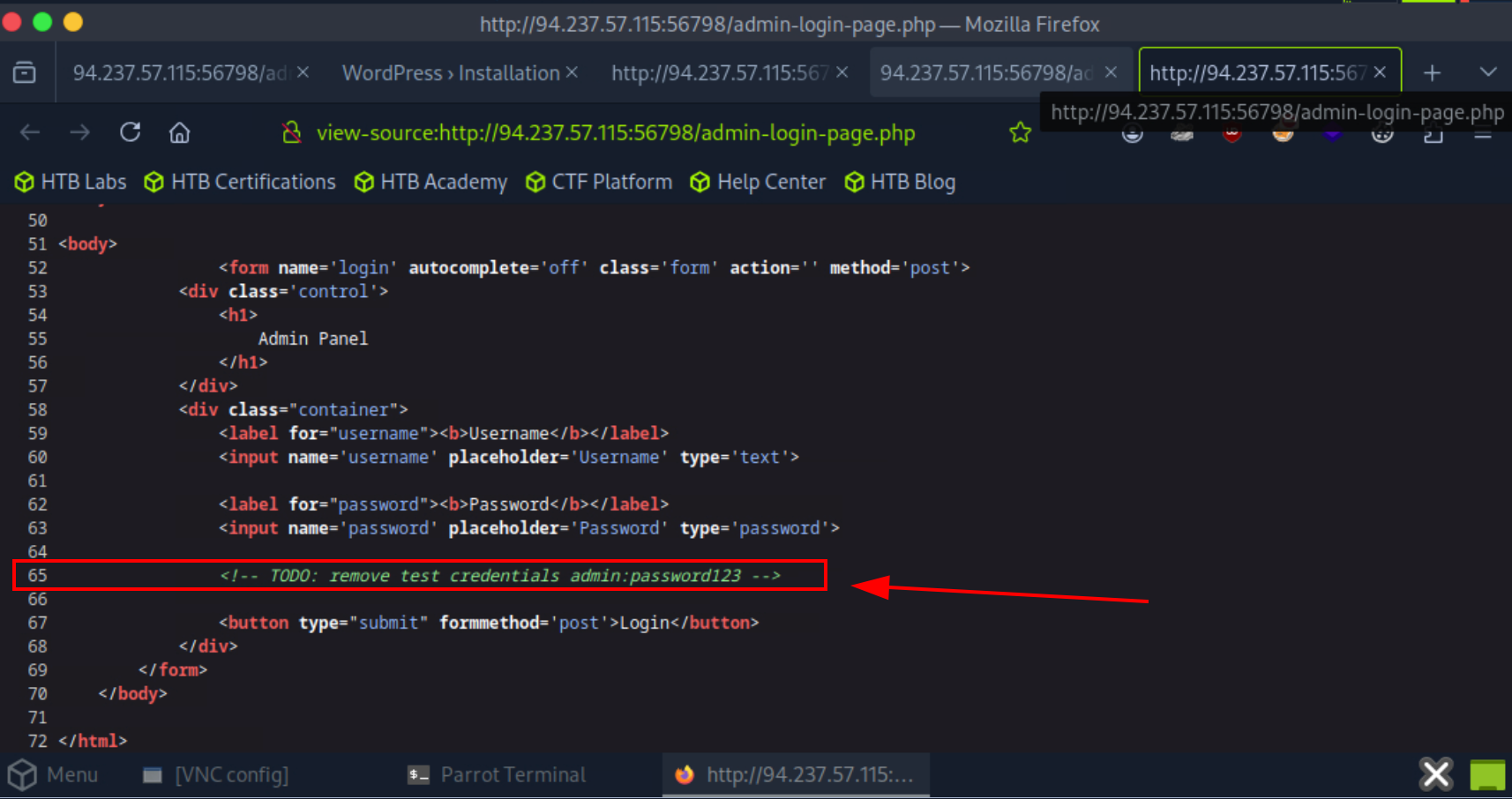
 After view the source and read about the source, we found an interesting comment in the source. This is a comment that include credentials username and password.
After view the source and read about the source, we found an interesting comment in the source. This is a comment that include credentials username and password.
 Now lets use this credentials to login in the site.
Now lets use this credentials to login in the site.
5. Flag
Try to use the credentials from comment in page source, and yes we success logged in in this site. The flag showed!!
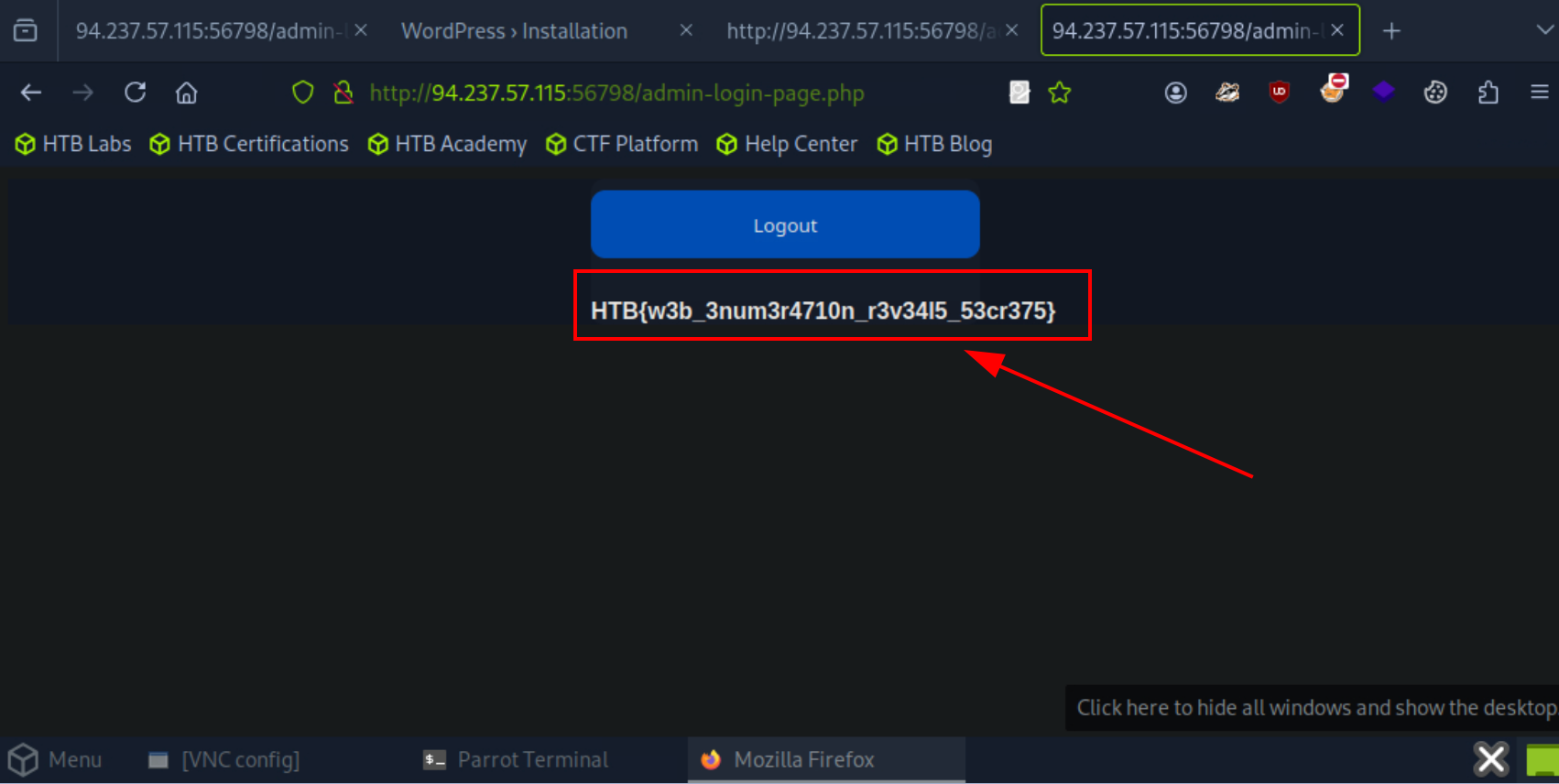
Submit the flag and we did it!