Introduction
This lab is vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
Solution
1. Find the request login and send to Burp Intruder
Open the web login page, and try to login with random username to trigger the login HTTP request. We will see the error message like this:
 Find the http request from
Find the http request from Proxy > HTTP history and send to Burp Intruder. Notice that in line 23 is a username and password that we input in the web page.
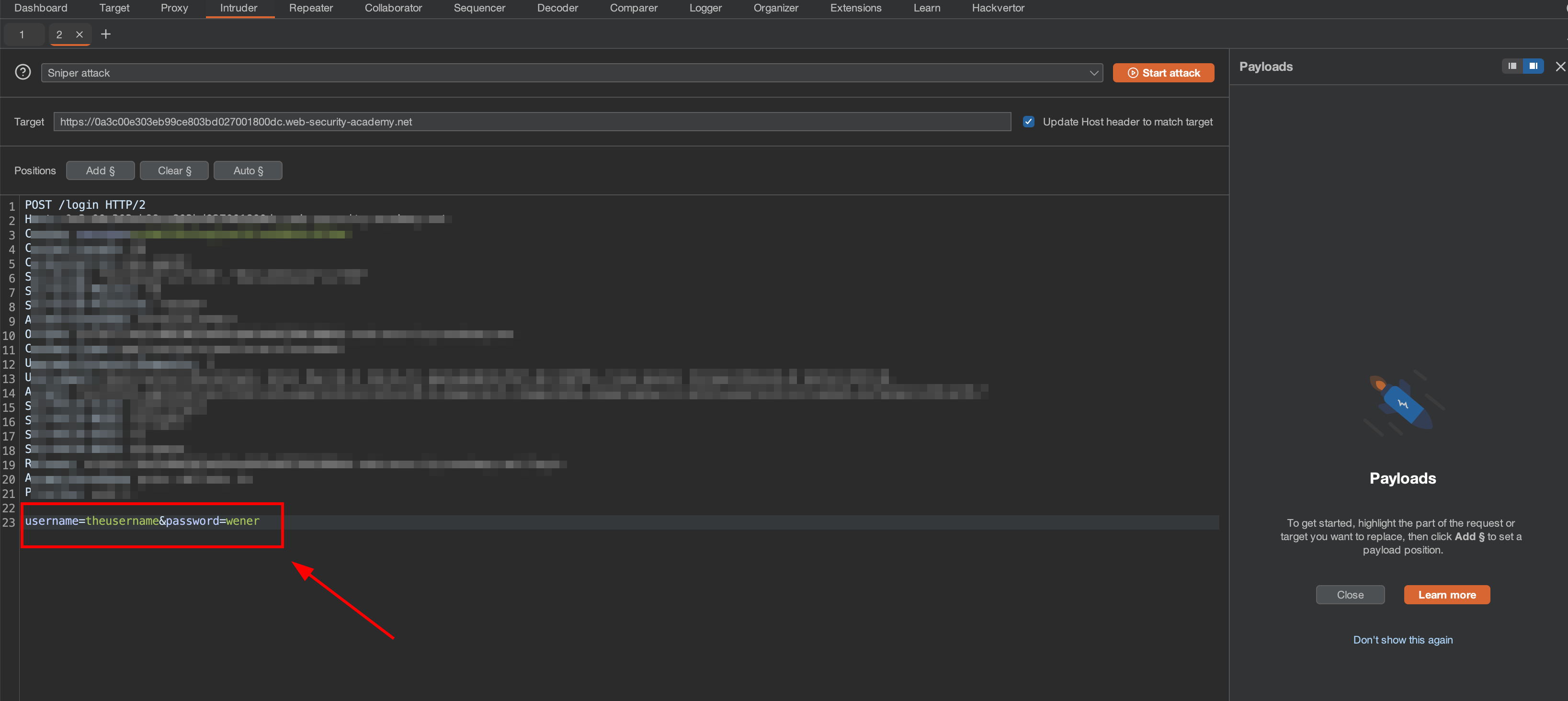
2. Find the valid username
Block the username value and click Add. Copy the username word lists and construct the payload.
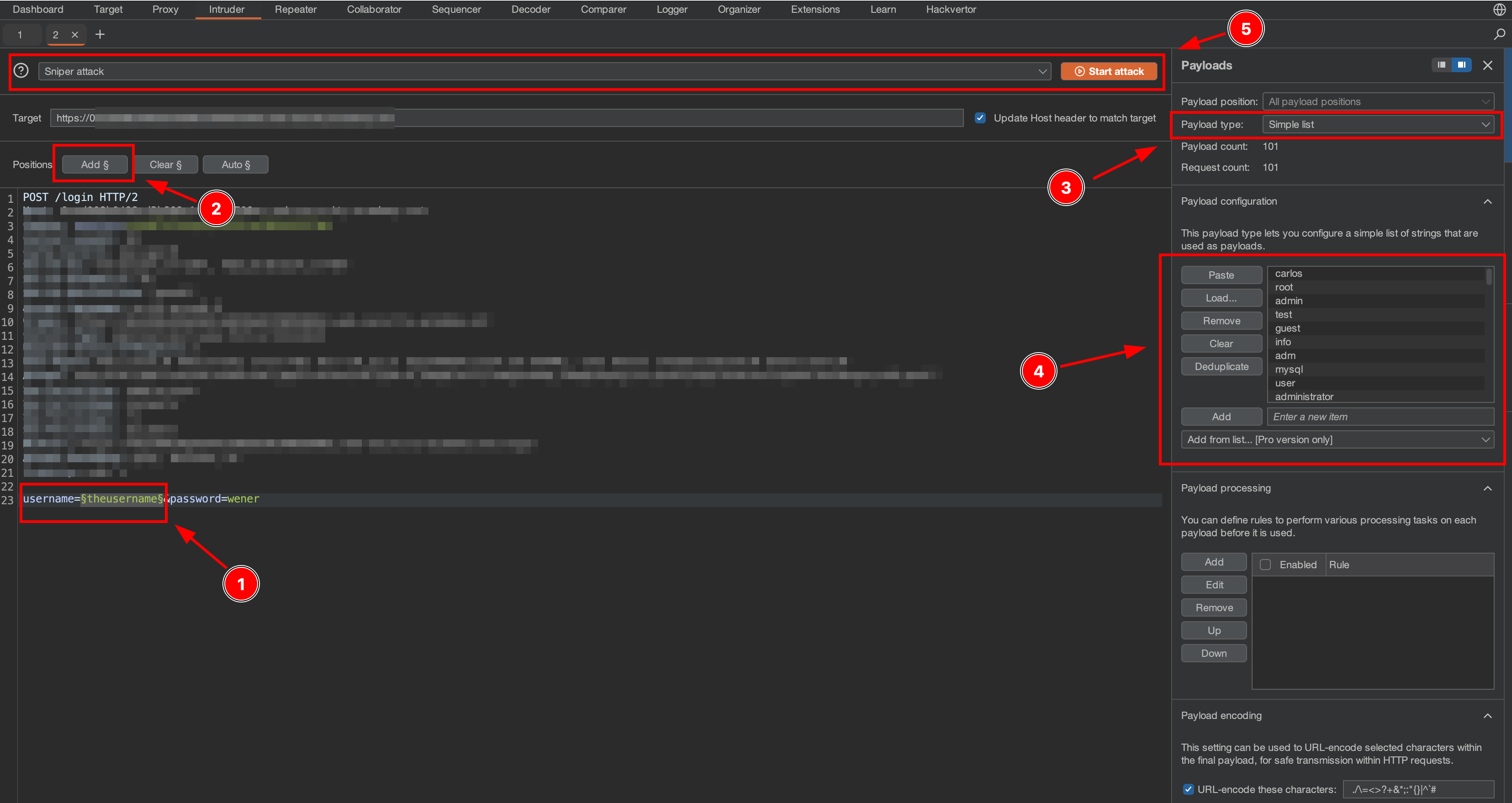 The steps look like this:
The steps look like this:
- Block the value of username
- Click Add
- Choose payload type as “simple list”
- paste the username wordlists (the wordlist you can copy from here)
- choose “sniper attack” and click “start attack”
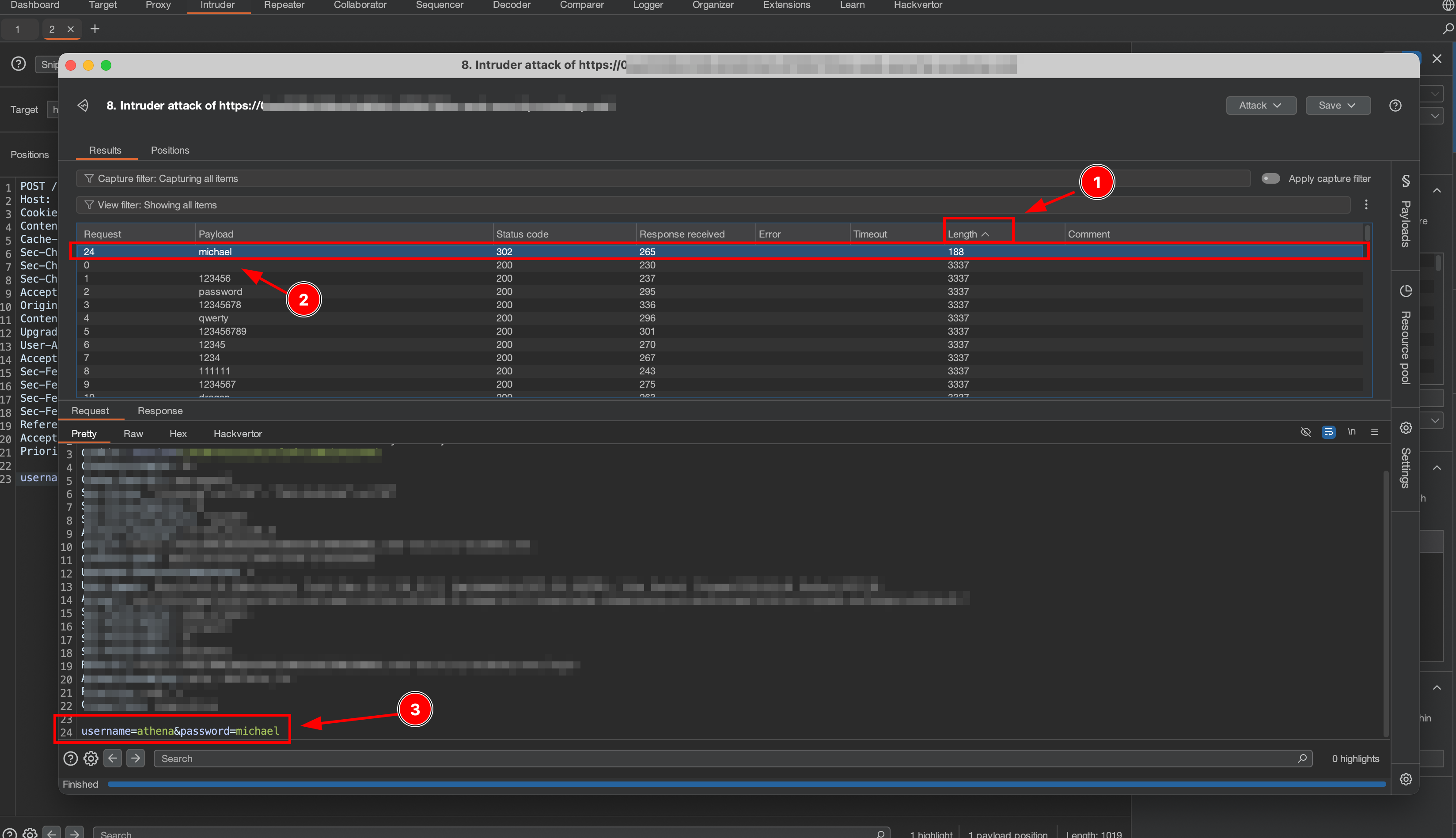
After the attack is finished:
- Click the column Length for sort the order with row value
- Click the request with username “athena”
- The response body is contain error message invalid password
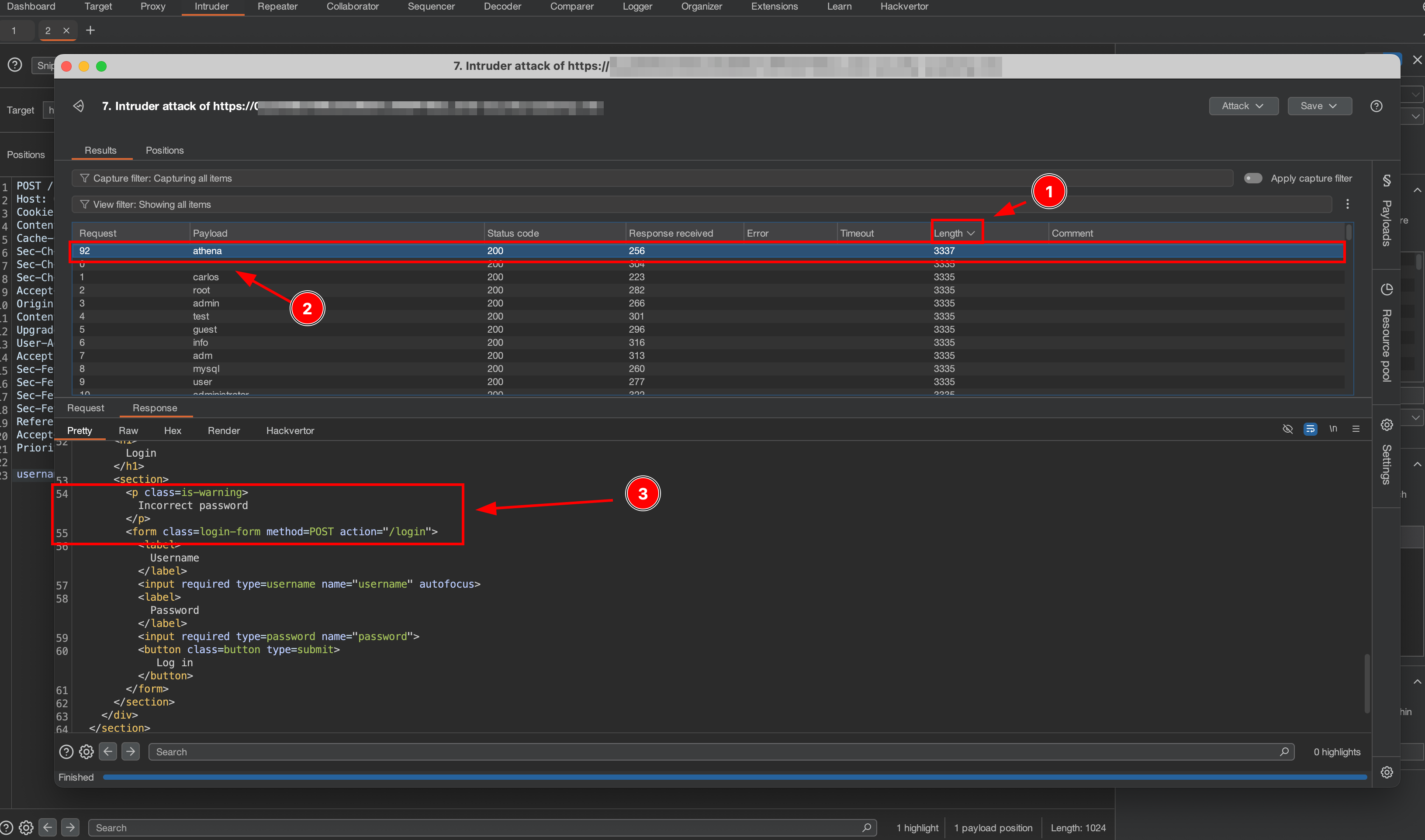 It indicate that the username “athena” is a correct username, but the password is incorrect. Next, we will use this username combined with password wordlists.
It indicate that the username “athena” is a correct username, but the password is incorrect. Next, we will use this username combined with password wordlists.
3. Find the valid password
The step is mostly same like previous step. But, in this step we use username named “athena” and using password wordlist from here for the password value. And click Start Attack.
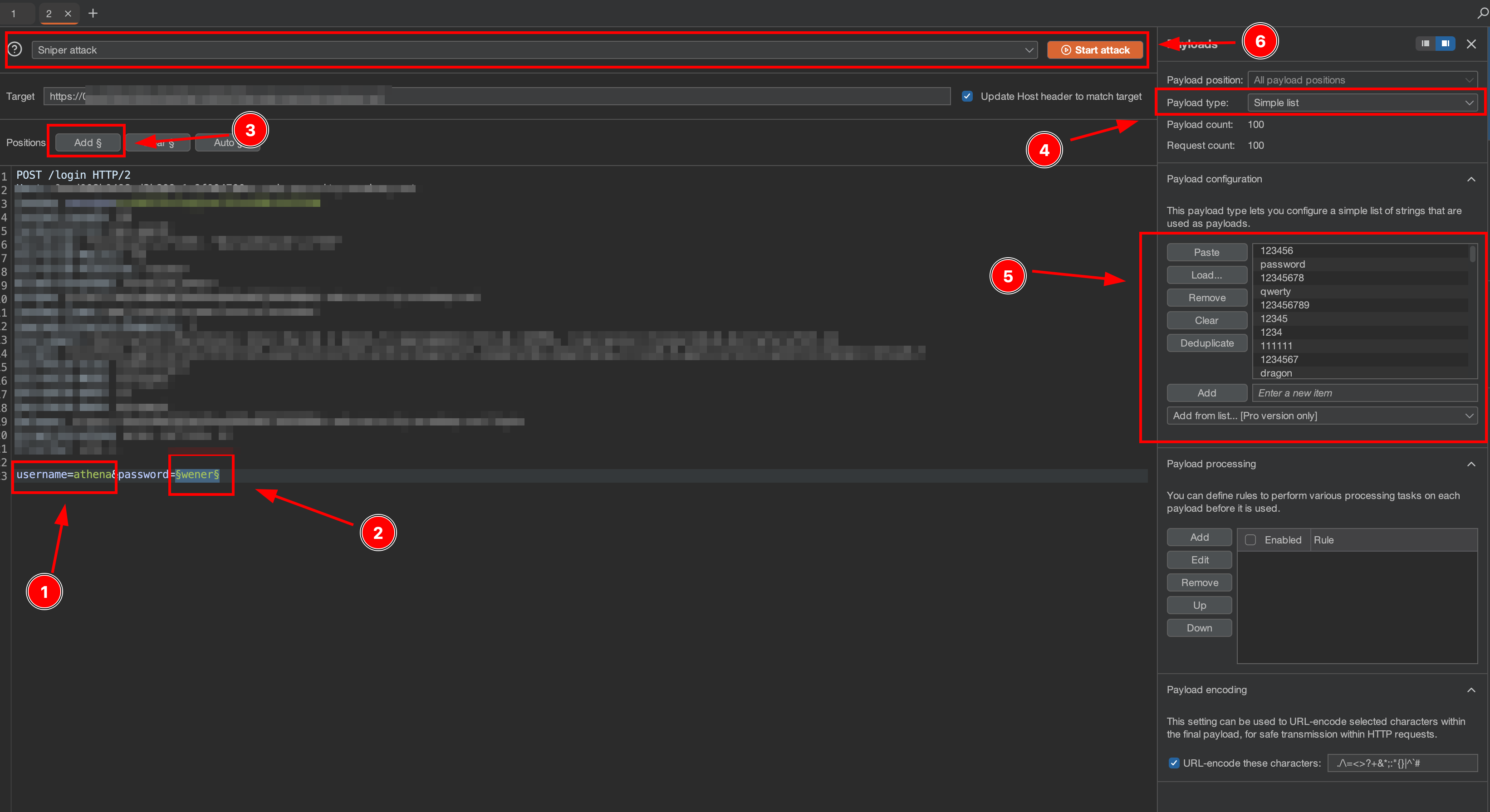 After the attack is finished, sort the “Length” column, and click the top request, in the request we found the correct password for user “athena”.
After the attack is finished, sort the “Length” column, and click the top request, in the request we found the correct password for user “athena”.
4. Login using username and password
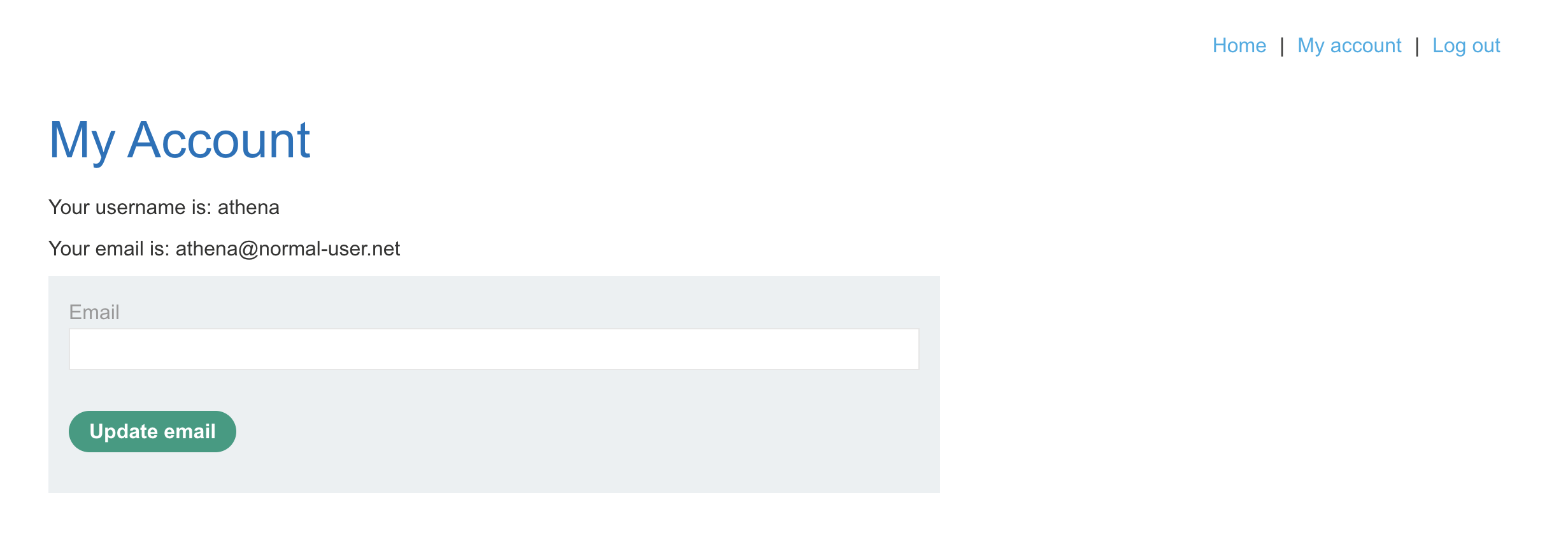
From previous step, we found that the valid username “athena” and the valid password “michael”, now try to login to solve the lab.
Thanks for reading
