Instruction
This lab contains a vulnerable image upload function. It attempts to prevent users from uploading unexpected file types, but relies on checking user-controllable input to verify this. To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner. You can log in to your own account using the following credentials:wiener:peter
Solution
1. Goal
Exfiltrate the contents of /home/carlos/secret via bypass Content-Type restriction.
2. Craft the php file
Because our target for exfiltrate/stealing data on the the file /home/carlos/secret. We craft the php file with this following code:
<?php echo file_get_contents('/home/carlos/secret'); ?>3. Try to upload the .php file as is
Try to make sure the validation by uploading the .php file first.
 As expected, we got error:
As expected, we got error:
Sorry, file type text/php is not allowed Only image/jpeg and image/png are allowed Sorry, there was an error uploading your file.
Based on the error message above, we now know about:
- Can use Content-Type
image/pngwhen upload file - Can use Content-Type
image/jpegwhen upload file - CANNOT use Content-Type
text/phpwhen upload file
4. Intercept and change request Content-Type
Because in previous error message we know that Content-Type must be image/jpeg or image/png , now we try to change this Content-Type using Burp Suite.
Intercept the request in Burp Suite and send to Repeater, after that change the Content-Type like below:
- From this

- To this

If you notice, we only change the Content-Type and not change other than that. After the Content-Type we changed to image/png from text/php, our file upload is success and the php web shell still uploaded.
5. Open Path
Back to My Account page and we’ve seen the UI indicate the broken image symbol, right click and click Open Image in New Tab it will open new browser tab.
 The path of new browser tab is looks like this
The path of new browser tab is looks like this {host}/files/avatars/webshell.php and we can seen the page that rendered with content on the that file.
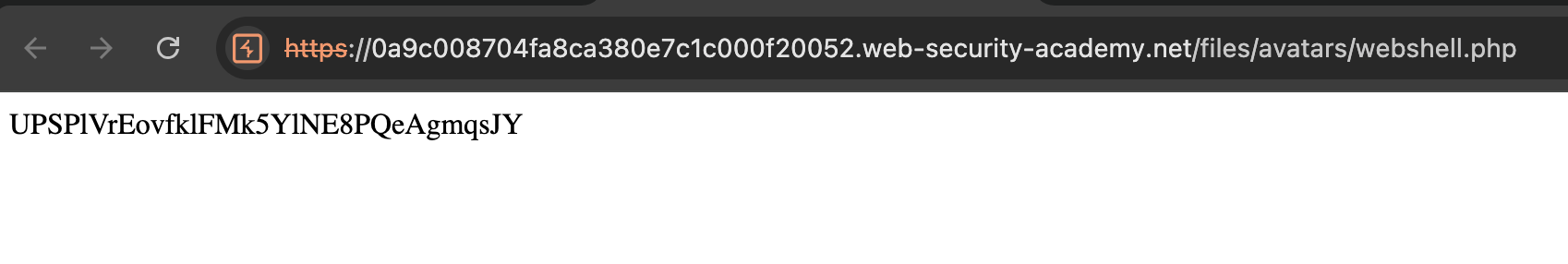 The value
The value UPSPlVrEovfklFMk5YlNE8PQeAgmqsJY is based on the file_get_contents('/home/carlos/secret');, When the script being executed, it will run function file_get_contents() and read the file /home/carlos/secret.
Thanks for reading
